
I recently visited the Flørli stairs in Lysefjorden, Norway, near where my grandfather spent his childhood, and looked up at 4,444 wooden steps stretching toward the top of a plateau through a steep, tree-covered hillside. It’s an old maintenance stairway used by workers at the turn of the century who were building a hydroelectric plant. The workers who climbed those stairs ascended from sea level to a height of 2,428 feet, often with 50-kilogram bags of concrete on their backs. It’s hard to imagine how they managed the task, but as I thought about what it takes to tackle such a thing daily, I realized it reflects a lesson that applies to those of us working to improve cybersecurity, particularly through deploying Zero Trust architectures. Just like climbing the Flørli stairs, reaching the top of the Zero Trust learning curve is accomplished one step at a time.
When I first started talking about Zero Trust, many people didn’t understand what it is or why they should deploy it. The principles of Zero Trust didn’t match what they were familiar with, and it took time to convince people that we needed to practice cybersecurity in a new way, since the way we’d approached cybersecurity before wasn’t working.
Now that more people understand what Zero Trust is about, I’m more likely to hear the objection that deploying it sounds overwhelming and people aren’t sure where to start. The thing I fight against now is doing nothing. It’s easier to keep things the way they are, easier not to start climbing those wooden stairs.
I’ll be honest. When I went to Lysefjorden, I went up 10 steps and said, “Okay, I’m done with this.” I didn’t need to reach the top to check that off my bucket list, so I didn’t keep going. The problem is that, for the workers who had to climb those stairs, reaching the top wasn’t about a bucket list. It was about doing the job they needed to do with the buckets they were carrying.
In cybersecurity, in a threat environment that’s constantly escalating, we can’t settle for keeping things the way they are. Organizations have to find a way to reach the top of those stairs.
We Need to Change How We Approach Deploying Zero Trust
I have worked in Zero Trust environments for well over a decade. I used to think that we should start deploying Zero Trust with the most sensitive data an organization needs to protect because those things are the most important. Experience now tells me that thinking was wrong, and we need to change it.
Deploying Zero Trust environments is based upon the concept of protect surfaces, the smallest possible reduction of the attack surface. A protect surface contains a single DAAS element (Data, Assets, Applications and Services), and these vary as far as how sensitive or critical they are.
The trouble with starting with the most sensitive protect surfaces is that they’re often too fragile and many people don’t know how they work. Starting there with Zero Trust frequently results in failures. Too often, when this happens, organizations blame these failures on Zero Trust. In fact, the problem is that no one in the organization has experience building Zero Trust environments.
To gain that experience, you have to follow the Zero Trust learning curve.
Following the Zero Trust Learning Curve
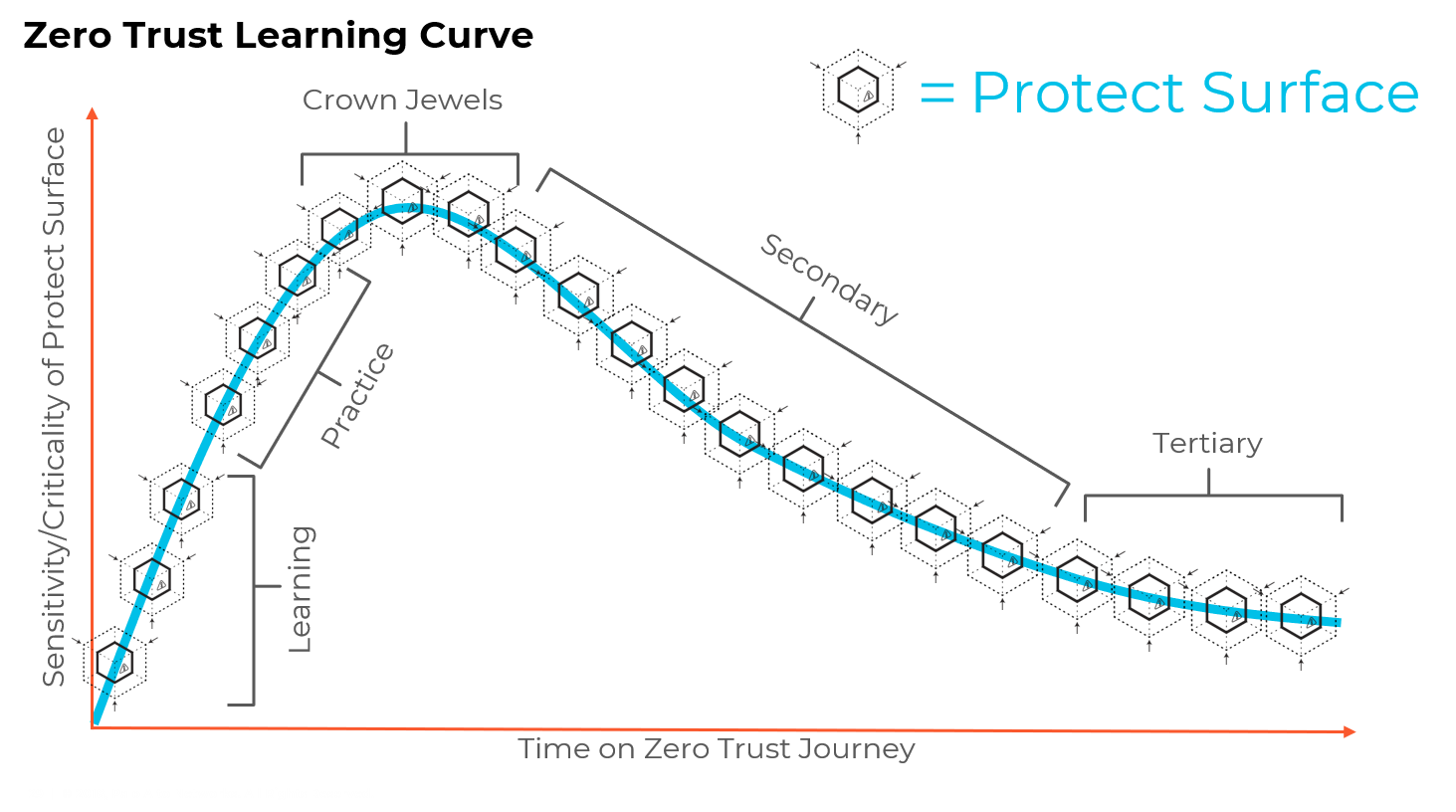
To start out deploying Zero Trust environments, an organization should consider two axes. The first is the sensitivity or criticality of the protect surface, and the second is the time you’re spending on the Zero Trust journey. Ideally, that second axis will stretch out for as long as your organization exists.
The first protect surfaces to work on are what I call learning protect surfaces. You need to start with a low sensitivity environment because you have to give people the ability to fail without retribution. Lab and testing environments are ideal for learning, but pretty much anything can work if it’s low criticality. You could even practice on the web page that has the specials for this week in the cafeteria.
Once you’re comfortable with the basic concepts of Zero Trust environments, you can move on to the practice protect surfaces. These are a little more sensitive, a little more critical, but they’re not the “crown jewels” of your organization. Remember you get to Zero Trust the same way you get to Carnegie Hall: “Practice, practice, practice.”
This way, before you touch the most sensitive protect surfaces in your environment, you’ve practiced and gained confidence in the mindset of Zero Trust. This is the peak of the Zero Trust learning curve.
Once you’ve protected your high-value assets, it’s smooth sailing going forward. From there, you can focus on less important assets, the secondary and tertiary protect surfaces. Eventually, you’ll end up in a place where you don’t have anything left that’s important enough to go into a Zero Trust environment.
The Zero Trust Journey Lasts a Lifetime
Zero Trust is a strategy that’s decoupled from technology. While technologies may adapt and change and you may need to update your environments as they do, the conceptual and strategic parts of Zero Trust won’t ever change. Once you follow the Zero Trust learning curve, you’ll be in a good position to continue protecting your organization using this mindset for as long as your organization exists.
No matter how daunting deploying Zero Trust may seem at first, my experience tells me that taking the right approach to the Zero Trust learning curve gets most organizations up to speed very quickly. One client told me, “We spent more time arguing about Zero Trust than we did deploying the first Zero Trust environment.”
Don’t be one of the organizations that never start the journey because they don’t figure out how to take the first step. Besides, when I think of what we do in cybersecurity and IT, it’s a lot easier than carrying 50-kilogram bags of concrete on your back, 4,444 steps, up to the top of a mountain.
For more information about how to deploy Zero Trust networks, download the whitepaper, “5 Steps to Zero Trust.”