As threat actor techniques continue to get more targeted and sophisticated, there is more pressure than ever on detection and response vendors to continually test and improve detection methods. The MITRE ATT&CK evaluations were created to test the detection capabilities of leading endpoint security vendors by emulating the real-world attack sequences of sophisticated advanced persistent threat (APT) groups from around the world.
In Round 2 of the MITRE ATT&CK evaluations, Cortex XDR was put to the test once again, this time against the tactics and techniques that have been leveraged by the threat actor group known as APT29 aka Cozy Bear, who are known for their stealthy, sophisticated and highly customized attacks. The evaluation involved two complete attack scenarios leveraging 58 unique techniques from the MITRE ATT&CK Framework. We are proud to announce that no other vendor achieved higher attack technique coverage than Cortex XDR in this evaluation with the powerful combination of automated product detections and enrichment from the Cortex XDR Managed Threat Hunting service.*
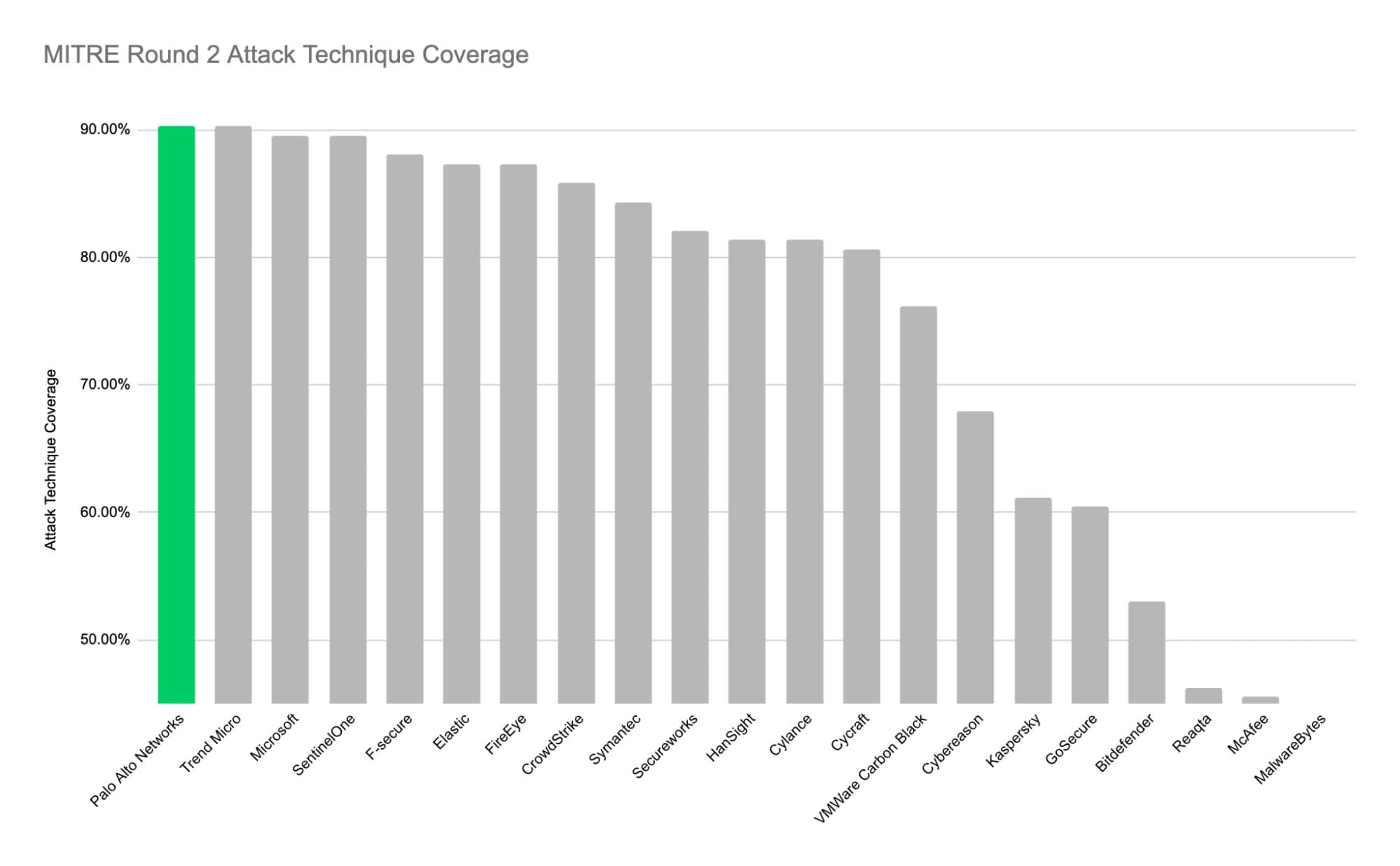
The results of this round emphasize the consistent best-in-class threat detection capabilities of Cortex XDR, which were demonstrated in the recent NSS AEP test and the 2019 MITRE APT3 evaluation. In the 2020 MITRE APT29 Evaluation, Cortex XDR was at the front of the pack both in the number of detections and in the specificity and accuracy of those detections compared to the 20 other endpoint detection and response products tested. To complement our strong performance in automated product detections, the Cortex XDR Managed Threat Hunting service further augmented our results with human expertise from our world-class threat hunting team, resulting in superior overall product and service coverage in this evaluation, with 90% of techniques detected.
Cortex XDR goes beyond traditional EDR approaches that rely on narrow endpoint-focused data sources to detect attacks. Instead, it validate alerts by providing holistic, accurate visibility across your entire enterprise. While the MITRE evaluation tested products’ abilities to detect activity beyond traditional endpoints, such as domain controllers and file servers, it stopped short of including other critical enterprise infrastructure, such as network and cloud sources, which we expect would have improved our results even further. We look forward to continuing to work with MITRE as they consider expanding the scope of their evaluation with the addition of prevention capabilities and new data sources to address the full scope of our XDR solution.
To take a deep dive into the MITRE APT29 Evaluation and how Cortex XDR performed, download our "Ultimate Guide to MITRE" white paper. You can also watch the replay of our “MITRE ATT&CK Round 2: Results Unveiled” webinar.
*Attack technique coverage in this context is defined as the highest number of attack techniques detected by the product or the MSSP service. Detection configuration changes that took place during the evaluation are counted as a miss, as these indicate adjustments by the vendor that could point to gaps in coverage. This methodology was applied universally to all vendors.