
We are proud to announce the Community Access edition of Cortex XDR Managed Threat Hunting, a powerful threat hunting service exclusively for our Cortex XDR customers. For a limited time, Community Access is available for free to eligible customers.
With Cortex XDR, Palo Alto Networks has delivered unmatched detection capabilities that run on high-fidelity integrated data from endpoint, network and cloud data sources. Now, we’re augmenting the power of Cortex XDR with a managed threat hunting service led by the globally renowned Unit 42 threat intelligence team to identify hiddens attacks that would otherwise go undetected. Our threat hunters apply human expertise augmented with big data analytics and comprehensive threat intelligence to surface malicious tactics, techniques and procedures hiding amongst billions of benign actions.
What Makes Cortex XDR Managed Threat Hunting Unique?
- Backed by Unit 42: The world-renowned experts, who lead the way in tracking adversaries and have uncovered major attacks like OilRig, will work around the clock to identify hidden threats in your network, endpoint and cloud assets.
- Unprecedented analytics: 7 trillion threat artifacts and 14 billion malware samples crowdsourced from 35,000+ organizations inform our industry-leading researchers and machine learning models.
- Clear and proactive: Gain clear direction with deep context on active threats and proactive impact reports to shut down emerging threats with confidence.
Threat hunting is not just a people problem. You need good data and analytics.
Don't miss your chance to take advantage of the Community Access edition of Cortex XDR Managed Threat Hunting. You can also access it directly within the settings menu of Cortex XDR.
Even More New Cortex XDR Capabilities
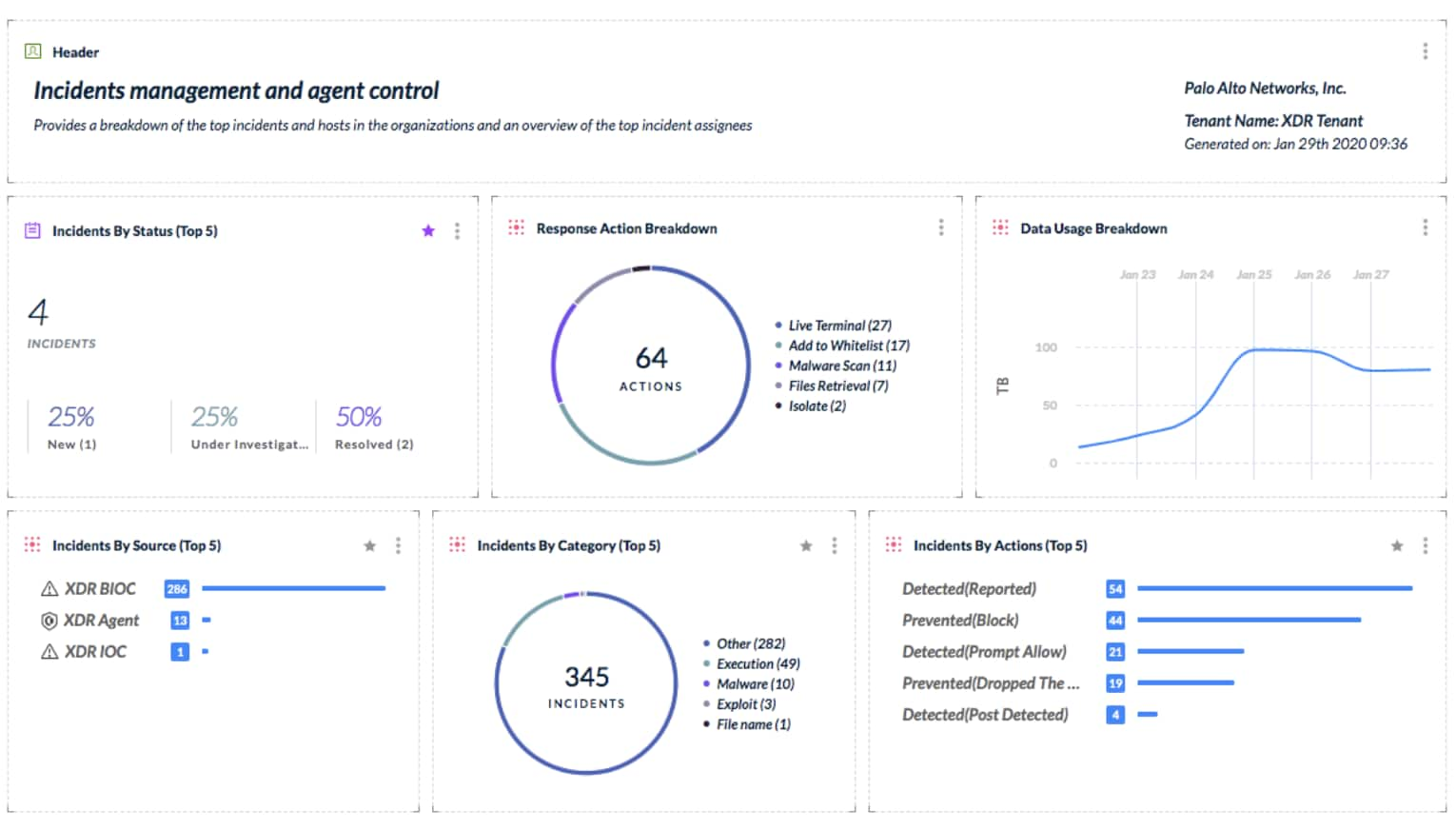
On the heels of the latest release of Cortex XDR, our R&D teams have already delivered several exciting new Cortex XDR features that further improve dashboarding, alerting and third-party integrations:
Enhanced visibility and reporting
To identify high-severity threats and connectivity problems, your analysts need dashboards tailored to their unique requirements. When reviewing security alerts, they must have rich investigative context at their fingertips.
In the February release, Cortex XDR has added six new dashboard widgets that allow analysts to monitor incidents by status, alerts by category or source, and much more. Analysts can build custom dashboards with flexible chart options to assess security status.
Improved integration with WildFire lets your analysts view WildFire Analysis Reports without needing to download a PDF file or leave the Cortex XDR management console. Analysts can click on a link in the Cortex XDR “Causality” window to examine process, timeline and network information gathered by WildFire. WildFire analysis, included standard with Cortex XDR, takes the guesswork out of malware analysis.
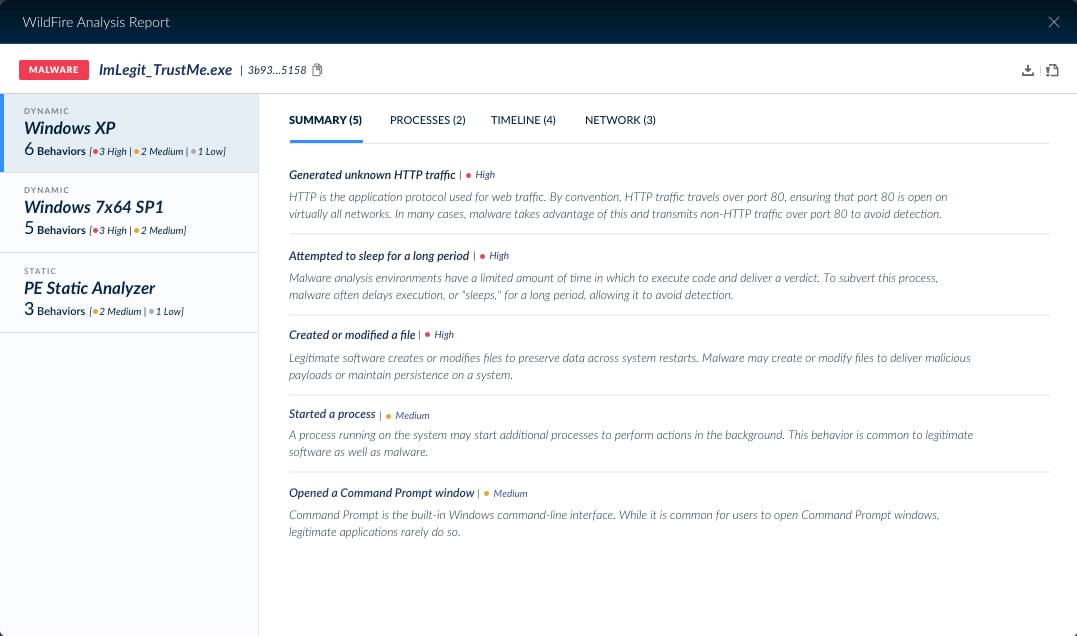
An integrated WildFire Analysis Report simplifies Cortex XDR investigations.
New APIs extend integration with third-party tools
Cortex XDR now supports flexible APIs to retrieve or quarantine files, scan endpoints and much more. Organizations can use Demisto or other third-party tools to coordinate responses or collect telemetry from many Cortex XDR agents at the same time. These public APIs also allow partners or managed service providers to use the administration tools of their choice for monitoring and management. The new APIs complement existing Cortex XDR APIs introduced in the December 2019 release.
Email-based alert notifications
Email-based alerts allow analysts to be notified instantly when security events occur. Analysts can now streamline alert management by configuring alert notification and aggregation settings from the Cortex XDR management console. They can also define the alert specifications, distribution lists and how often to send notifications in the “Settings > Alert Notifications” page.
Coordinated response across multiple endpoints
To shut down malware outbreaks, security teams must act quickly. By locking down multiple endpoints at once, Cortex XDR administrators can prevent the spread of dangerous attacks across the organization. Cortex XDR now allows administrators to isolate multiple endpoints simultaneously, cutting response time and eliminating repetitive administrative tasks.
Other enhancements introduced in February include encrypted and password-protected PDF reports and agent management features. To learn more about these new features, see the Cortex XDR release notes.