This post is also available in: 日本語 (Japanese)
In our extensive work with security teams around the world, we’ve seen the best and the worst security operations (SecOps) practices. Despite a wide range of cybersecurity strategies and investment levels, we’ve found that most enterprise security programs have lots of room for improvement to better prevent, identify, investigate and mitigate threats with speed and confidence. Even mature Security Operations Centers (SOCs) commonly struggle with alert fatigue, staffing turnover, and complicated manual processes, all of which take away valuable time that they could be spending on investigations and process optimization.
The first measure to make meaningful improvement is to take a step back and do an honest evaluation of how your security operations are structured and how they’re serving your business goals.
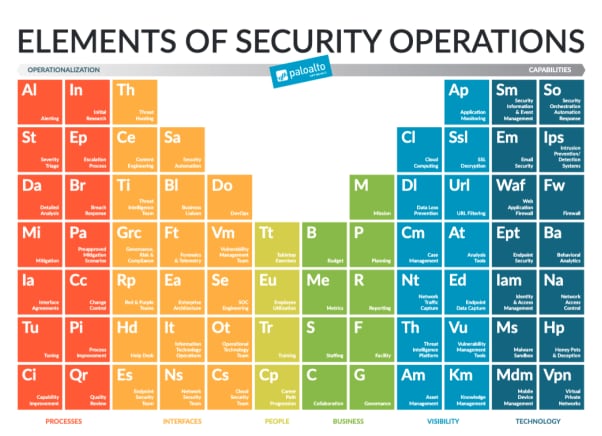
To help with this evaluation, we’ve condensed the considerations that go into building efficient and scalable security operations into six fundamental pillars. Each of these pillars contain a number of building blocks that we describe in-depth in our book, “Elements of Security Operations.” By evaluating your security operations against each of these pillars and their building blocks, you can assess your capability gaps and evolve your security operations to provide better and faster prevention and remediation.
1. Business
The Business pillar defines the business objectives and management strategies of the security operations team. Business questions that must be answered:
- Mission: What are we doing?
- Planning: How are we going to do it?
- Governance: How are we going to manage what we are doing?
- Staffing: Who do we need to do this?
- Facility: Where are we going to do this?
- Budget: What will it cost to do this?
- Metrics: How will we know it is working effectively?
- Reporting: How will we track activity and provide updates?
- Collaboration: How will we communicate and track issues with the rest of the business?
2. People
The People pillar defines the humans who will be accomplishing the goals of the security operations team and how they will be managed. Questions that must be answered:
- How will we find staff and train them to fulfill their roles?
- What will we do to retain them?
- How will we manage the workloads of the staff?
- How will we validate the efficacy of the actions of the staff?
3. Interfaces
The Interfaces pillar defines what functions need to be involved to achieve the stated goals. Security operations is not a silo and needs to work with many other functions of the business. We describe each of these interactions as “interfaces,” and these should be defined so expectations between groups are clearly stated. Each group will have different goals and motivations that, when understood, can help with team interactions. Identifying the scope of responsibility and separation of duties will also reduce friction within an organization. Questions that must be answered:
- What other functions of the business impact security operations?
- What other functions of the business does security operations impact?
- How will the security operations team work alongside these other functions?
- Who has ownership of responsibilities and are there service-level agreements (SLAs) that need to be documented?
- At what interval will these interfaces be reviewed and updated?
4. Visibility
The Visibility pillar defines what information the SecOps function needs access to. This includes security and systems data, as well as knowledge management content and communications through collaboration tools. Questions that must be answered:
- What primary security data is needed?
- What contextual data is needed?
- How often does this data need to be refreshed?
- What knowledge base information needs to be accessed?
- How will the security operations team see activity in the SOC?
- How will external teams see activity in the SOC?
5. Technology
The Technology pillar defines what is needed to achieve visibility into the information needed in the security operations organization. It is important to note that each element should not be thought of as a different tool but rather a capability that should be achieved with the given technology stack. Technologies and capabilities change rapidly, so these are the most fluid elements of a security operations team.
There is a glut of siloed tools in the industry that lead to a variety of issues, including extensive vendor management, limited feature use, duplicate functionality, and sometimes, end-user degradation. We’re seeing a shift, with organizations moving away from best-of-breed siloed tools toward platforms that provide capabilities needed in the SOC without the need for installation and maintenance of different tools. Questions that must be answered:
- What capabilities are required to achieve the necessary visibility?
- What technology will be used to provide these capabilities?
- Who will be responsible for the licensing, implementation and maintenance of the technology?
- How will technology and content updates be requested and performed?
- What updates will be carried out automatically and at what interval?
6. Processes
The Processes pillar defines the processes and procedures executed by the security operations organization to achieve the determined mission. Questions that must be answered:
- What processes need to be defined?
- Where will the processes and procedures be documented?
- How will this documentation be accessed and socialized?
- Who will have responsibility for keeping this documentation updated?
- How often will the processes need to be reviewed and updated?
By answering the questions from each of the above pillars, you will have an outline to assist in the improvement of your SecOps functions. For additional analysis of the considerations that go into each of these questions, download a free copy of our book, "Elements of Security Operations."
Watch for future posts in Kerry Matre's series on "Elements of Security Operations." Next up: "Do Your SOC Metrics Incentivize Bad Behavior?"