This post is also available in: 繁體中文 (Chinese (Traditional)) Nederlands (Dutch) Français (French) Deutsch (German) Italiano (Italian) 日本語 (Japanese) 한국어 (Korean) Español (Spanish)
Low TCO. Faster Time to Resolution. Immediate Security Value. Check!
Apttus was born in the cloud. We provide AI-driven SaaS offerings to our customers, including Quote-to-Cash, Contract Management, Digital Commerce and Supplier Relationship Management solutions. Our “all in” cloud approach has helped us better serve our more than 700 customers around the globe.
Some organizations still have a difficult time understanding how to run modern cloud infrastructure. So, understandably, they take the crawl before you walk, walk before you run approach. This looks something like: Take a lift-and-shift approach and migrate applications “as is” to the public cloud infrastructure (IaaS); optimize key components of the migrated application to leverage the managed services (PaaS) on offer in the public cloud; et al.
We chose to bypass the first two stages and run headfirst into cloud, taking advantage of the benefits provided by Azure, primarily, and AWS. We can do more with less, taking advantage of these platform-as-a-service (PaaS) options. But we needed a way to ensure secure access to our cloud infrastructure and applications for our global operations.
What Business and Security Issues Were We Looking to Solve?
In a nutshell, we needed fast, reliable and secure access to our cloud infrastructure driving our business and services, and we needed to ensure that we could quickly debug and resolve customer issues. Before we deployed Palo Alto Networks VM-Series Virtualized Next-Generation Firewalls, we faced two key security challenges.
Lack of centralized cloud access management
We create pods – essentially a collection of cloud resources needed to create a service and run our solutions. With each pod, we spin up a virtual machine (VM), which acts as jump host and gives operations teams access to the pod. Today, we have over 100 pods, and each pod access is time and resource intensive. The existing access management model does not provide visibility or control and remains a resource hog. A significant amount of time is wasted, and in business, time wasted is money lost.
Slow, insecure and hair-pinned cloud access model
We enforce centralized VPN usage for accessing cloud resources. Our users and employees would go through our corporate office to allow them to connect with single sign on (SSO). Then, they would connect from the corporate office to the data center. Given our team is global, with users and branches in India and several other countries, this introduced latency and slow connectivity into the system. As such, we couldn’t effectively troubleshoot, and it became increasingly difficult to run the business.
Palo Alto Networks VM-Series: A Decentralized Access Gateway to Cloud Resources
The old way of doing things simply wasn’t working. So, we spearheaded an initiative to develop an architecture where operations teams weren’t required to route through the corporate office as well as eliminate the need for a jump host in every pod. At the heart of this new security design sat Palo Alto Networks VM-Series. We deployed the GlobalProtect subscription on our VM-Series Virtualized Next-Generation Firewalls to act as the access gateway, and we’re using Panorama as the centralized security manager. Because the VM-Series connects directly into Azure AD for central user termination, we are now able to manage access and use a single identity source. Further, we gain granular visibility, control and the ability to segment and isolate pods from each other.
Who Cares? Let’s Talk Outcomes
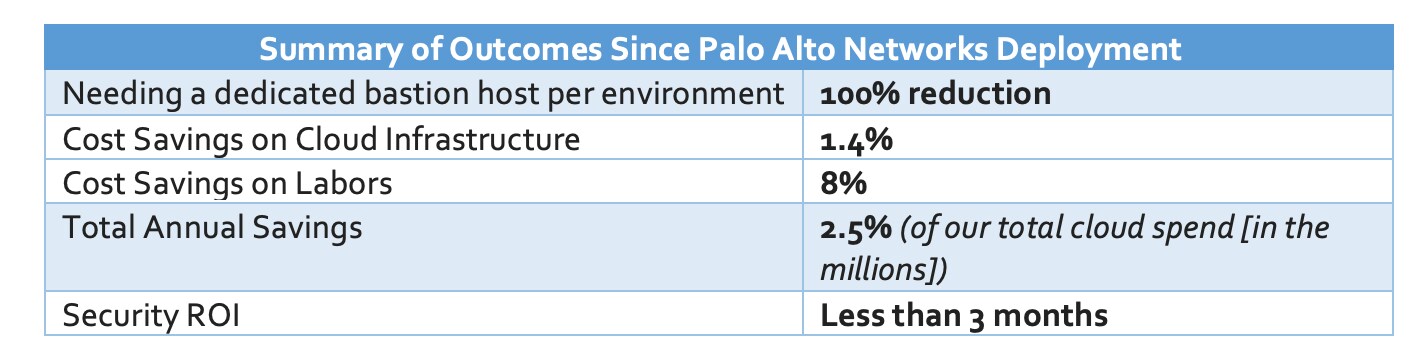
Since deploying Palo Alto Networks VM-Series in the cloud, we’ve seen significant savings in the amount of time required to pinpoint customer issues and resolve them. But that’s not all; check out the summary of cost savings and ROI below:
Obviously, there are several cloud firewalls available in the market. We chose Palo Alto Networks for 3 distinct reasons:
- Palo Alto Networks VM-Series has native integration with Azure AD. The integration with Azure AD in the cloud was crucial for Apttus. We’re able to centralize control of all user on/off boarding with Azure AD SSO, including activity and audit trails.
- The ability to manage the firewalls centrally through Panorama was hugely beneficial. Managing all firewalls is essential to keep configuration state and all firewall software up to date. The VM-Series also integrated with our SIEM system for additional security monitoring.
- The VM-Series is deployable through infrastructure as code (IaC). Our cloud infrastructure deployment is done as “infrastructure as code.” We’re able to programmatically decouple and deploy the VM-Series, along with the rest of the infrastructure components, in the cloud within minutes. It establishes an idempotent practice across all our regions.
If Nothing Else, Remember These 3 Key Things
As I mentioned earlier, we dove headfirst into the cloud running our apps on cloud-based modern infrastructure. And we rely on Palo Alto Networks to enable us to quickly and securely drive our business forward. As you think about your security and business evolution, I want to leave you with a few key thoughts and recommendations:
- With security, separate operations from IT: If you don’t, you’re likely to sacrifice on the agility gains that the cloud affords. It’s not necessary to go through the same paper processes on both sides of the fence. This is especially true for large organizations where it could take weeks, or even months, to fully cross the t’s and dot the i’s.
- You can scale security in cloud. I implore you, you don’t need as many access points (or Bat-Signals as I like to refer to them) to get into your system quickly and securely. Take advantage of cloud-native services like Azure AD – it was built to scale. You can easily authenticate your users within the cloud – no connection back to on-prem required.
- Choose security offerings that can be managed as IaC. We’ve had great success with Palo Alto Networks using infrastructure as code. We achieve high levels of security, low latency and improved time to resolution for customer support.
But you don’t have to take my word, you can take a test drive in your own environment. Sign up on the Azure Marketplace.