This post is also available in: 简体中文 (Chinese (Simplified)) 繁體中文 (Chinese (Traditional)) 日本語 (Japanese) 한국어 (Korean) Português (Portuguese (Brazil))
We are pleased to announce the results of an independent test that demonstrate the value of our recently launched Cortex XDR product in combination with Traps. The evaluation, which used the MITRE ATT&CK framework, shows that Cortex XDR and Traps provide the broadest coverage with fewest missed attack techniques among 10 Endpoint Detection-and-Response (EDR) vendors.
Broadest Coverage Across Attack Techniques
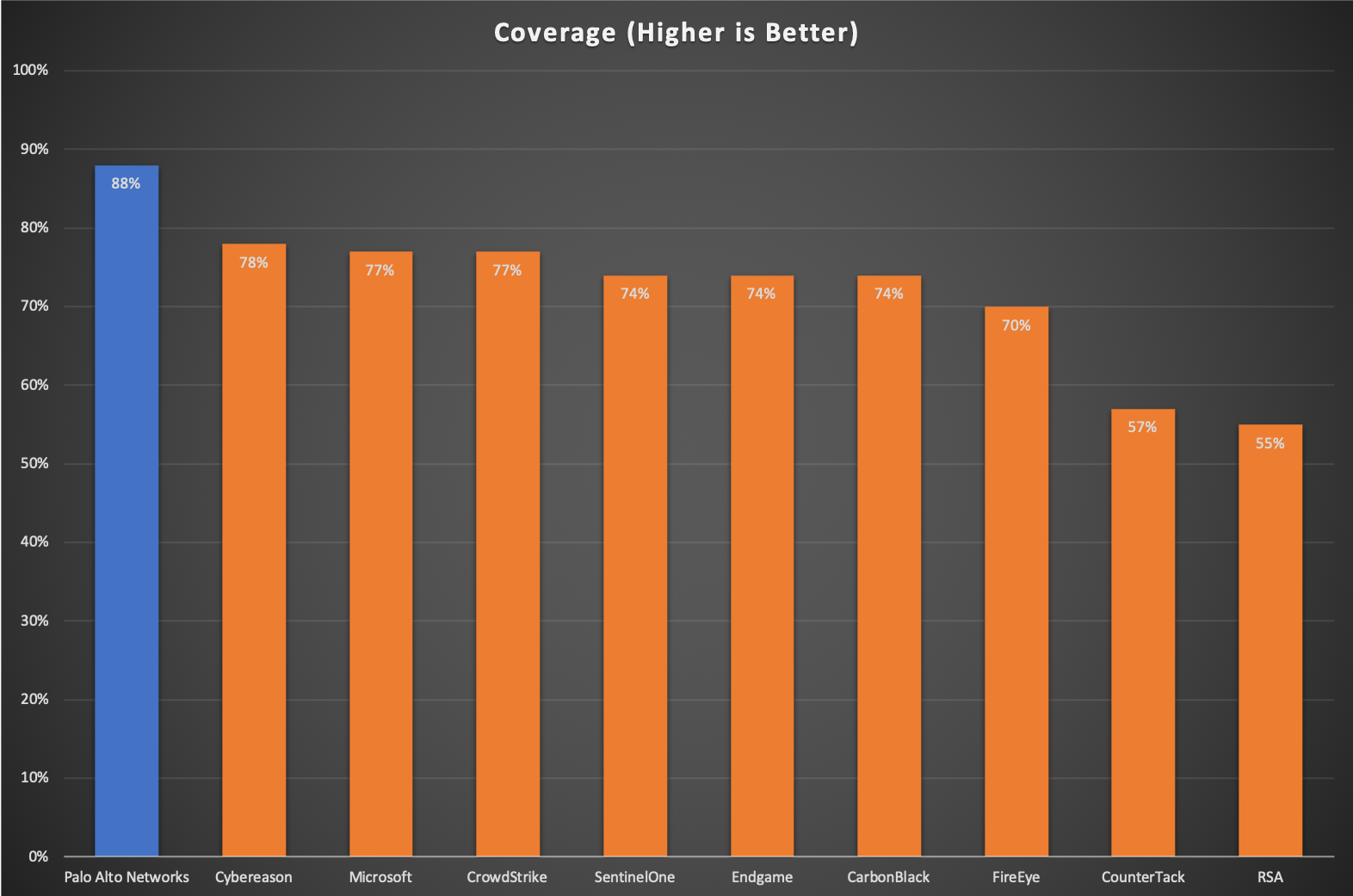
Cortex XDR and Traps provide the best endpoint visibility and the highest coverage across different attack techniques, according to the MITRE ATT&CK results. Coverage puts emphasis on the ability to gather telemetry across 136 attack techniques, generate real time alerts and provide enrichment for threats. The test results show that Cortex XDR and Traps provide coverage for 121 of the 136 techniques, more than any other vendor.
This chart was created by Palo Alto Networks to quantify vendor efficacy with the MITRE ATT&CK evaluation.
Automated Detection Reduces Missed Attacks
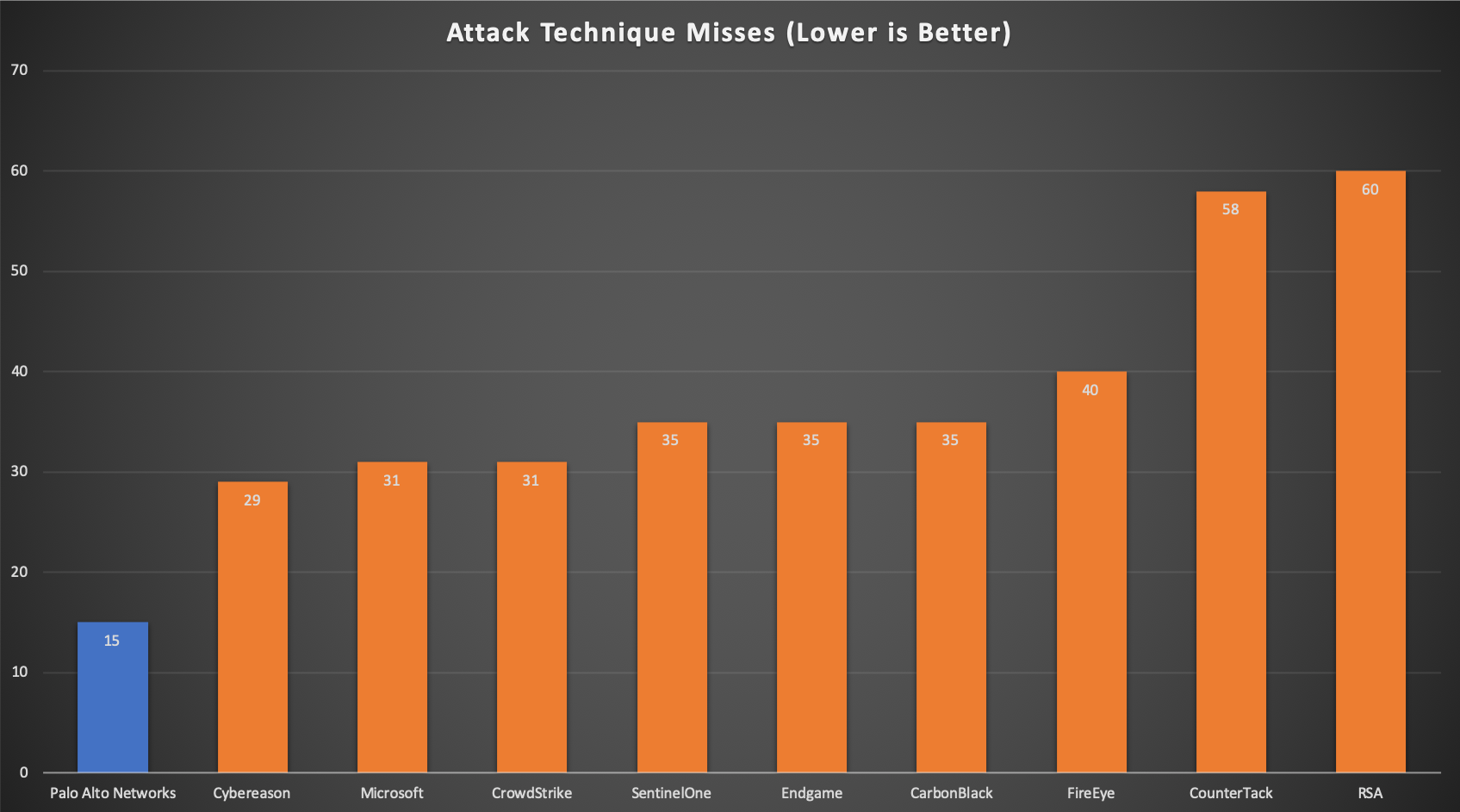
When it comes to threat detection, we strive to automate the process because relying on humans for detection can yield inconsistent or delayed detections. The MITRE testing validates this approach. Cortex XDR and Traps had the best detection coverage with zero delayed detections compared to other vendors who relied on a human process. The highly automated AI approach provided more coverage and more consistency with no delays.
This chart was created by Palo Alto Networks for quantifying vendor efficacy with the MITRE ATT&CK evaluation.
About Cortex XDR
Cortex XDR is the first detection and response product that natively integrates network, endpoint and cloud data to stop sophisticated attacks. This helps organizations reduce the mean time to detect and respond to attacks. MITRE specifically tested endpoint-only capabilities in a version of the product with no additional managed services. Palo Alto Networks worked with MITRE Corp, a non-profit that developed the widely used ATT&CK framework for evaluating detection and response products.
MITRE's ATT&CK framework provides an extensive list of capabilities and techniques that attackers have used in various real-world attacks. Organizations can use this framework to evaluate the efficacy and efficiency of their security controls. Their first-round evaluation reproduced the attack vectors of the APT3 group. MITRE releases raw results, but does not score, rank or produce quantitative analysis of the results. Forrester Research created a set of scripts to help score the results, which we have used to illustrate how Cortex XDR ranks under coverage, missed techniques and alerts. For more information on Forrester’s methodology, visit the Forrester blog here.
Conclusion
MITRE has developed an excellent framework that helps security operations team evaluate vendor products across the full breadth of detections and investigations. Based on the latest test results, we encourage customers who are evaluating an EDR project to reach out to Palo Alto networks to understand the MITRE framework, the techniques used in the testing, and how to interpret the results.
Customers face a challenge in their ability to detect threats when they have unmanaged devices or devices where they cannot install an endpoint agent. It is important to complement the endpoint data with network data so customers can expand coverage against threats across their entire digital domain. Cortex XDR and Traps deliver on this vision. We plan to engage MITRE in a second round of evaluations to include data collected beyond just endpoints.
To learn more about Cortex XDR and Traps, please visit the Cortex XDR product page and the Traps product page. The full results of all participating vendors, including Palo Alto Networks, can be found here.