This post is also available in: 简体中文 (Chinese (Simplified)) 繁體中文 (Chinese (Traditional)) 日本語 (Japanese) 한국어 (Korean)
While ransomware is not new, major attacks like WannaCry, Petya/NotPetya and, more recently, TrickBot have shown that existing prevention methods have become ineffective at preventing advanced ransomware attacks. Attackers have evolved their approach and use of malware to become more sophisticated, automated, targeted and highly evasive.
While WannaCry first hit almost two years ago, it was so effective that we continue to see breaches in the news attributing this dangerous malware. WannaCry was and continues to be effective because it uses a combination of malware and exploits to accomplish its tasks. First, it exploits a vulnerability in the Microsoft SMB protocol to achieve kernel-level privileges. Part of what makes this attack stealthy is the use of a kernel APC (asynchronous procedure call) attack. Attacks against the kernel have been around for some time, are well-known, and can be protected against. Kernel APC attacks, however, are a different class of attack. These don’t attack the kernel to gain privileges. Instead kernel APC attacks already have kernel privileges and use them to carry out their objective, in this case by making legitimate programs execute malicious code rather than their own legitimate code.
From the end user’s view, the ransomware screen locks everyone out so they cannot see any additional activity going on, on their endpoint. At the same time, the malware continues to spread east-west, infecting as many vulnerable machines as it can, both internally and externally.
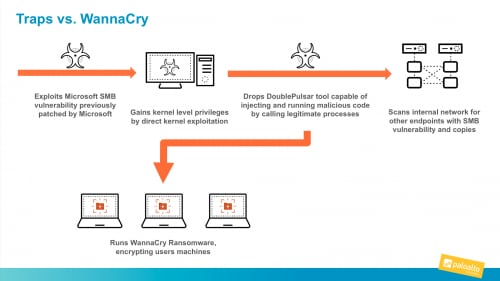
Simplified WannaCry attack sequence
Enter Palo Alto Networks Traps. Traps advanced endpoint protection combines multiple methods of prevention against known and unknown malware, ransomware, and exploits to stop the execution of malicious programs before an endpoint can be compromised. By putting protections at critical stages of the attack lifecycle, Traps is able to prevent ransomware attacks regardless of operating system, whether an endpoint is online or offline, or connected to the corporate network or not.
Leading up to the WannaCry outbreak, endpoints protected by Traps were able to detect and shut it down in a number of places in the attack lifecycle. First, Traps would have detected the exploit technique when kernel privileges attempted to be escalated to the user level. As soon as Traps had detected that action, it would have shut down the attack. If that didn’t work, the malicious process protection module would have detected and stopped the parent process spawning a child process. If the threats were not detected by the previous modules, the agent would have detected the attack and stopped it by identifying it as a known threat, through local analysis, through the ransomware protection module, or through a detailed WildFire analysis.
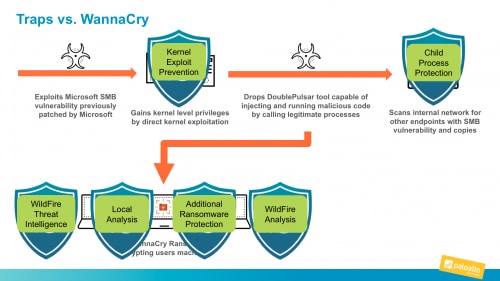
During and after the WannaCry attack, there were no known Palo Alto Networks customers infected by WannaCry because the threat was submitted to the WildFire malware prevention service almost a month prior to the May 12, 2017, attack on the National Health Service in the U.K. When we look into AutoFocus, we see that WannaCry was first discovered on April 16, 2017, and protections were created and distributed to all Palo Alto Networks firewalls, endpoints, etc.
At the end of the day, an attacker must be successful at every stage of the attack lifecycle, whereas Traps advanced endpoint protection only has to be successful in one stage to shut down the attack.
To learn more about the essential requirements for endpoint protection, view this on-demand webcast to learn how Traps simplifies protection and reduces the cost of securing resource sensitive environments.