Thousands of new software vulnerabilities and exploits are discovered each year, requiring diligent software patch distribution by software vendors on top of patch management by system and security administrators in every organization. This regular flow of patches and updates often lands on “Patch Tuesday,” the monthly or semimonthly day when Microsoft releases security patches for its software.
Patching is a critical part of a sound endpoint protection strategy. However, patch management only protects an organization’s endpoints after vulnerabilities are discovered and patched. Delays of days, weeks or longer are inevitable as patches for newly discovered vulnerabilities must be developed, distributed, tested and deployed. Although patch management is an important aspect of any information security program, much like signature‐based anti-malware detection, it is an endless race against time that offers no protection against zero‐day exploits. Vulnerability exploits, however, constitute the primary reason patches are applied.
A great deal of attention has been paid to malware since the earliest days of computing, and although malware prevention is critical to endpoint protection, it is only one part of a comprehensive endpoint security strategy. Exploit prevention is equally important but less understood.
Understanding Exploit Techniques
Many advanced threats work by placing malicious code in seemingly innocuous data files. When these files are opened, the malicious code leverages unpatched vulnerabilities in the native application used to view the file, and the code executes. Because the application being exploited is allowed by IT security policy, this type of attack bypasses application whitelisting controls.
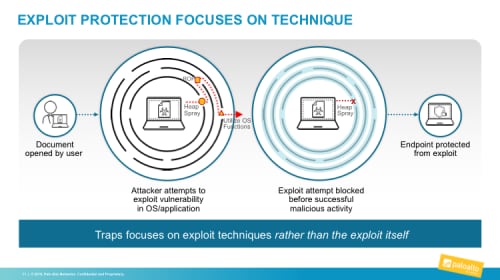
Although there are many thousands of exploits, they all rely on a small set of core techniques that change infrequently. Regardless of the exploit or its complexity, for an attack to succeed, the attacker must execute a series of these core exploit techniques in sequence, like navigating a maze to reach the goal.
Figure 1: Focus on exploit techniques, not exploits themselves
Traps focuses on the core techniques all exploits use and, by rendering those techniques ineffective, negates application vulnerabilities whether they are patched or not.
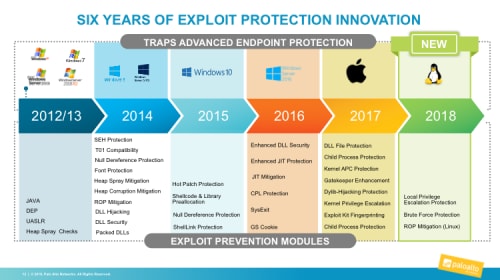
Figure 2: Six years of innovative exploit prevention
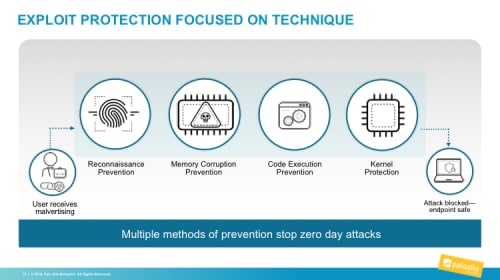
Naturally, it’s still best to keep up with the latest security patches. However, Traps gives you the option, and confidence, to hit “pause” on Patch Tuesday, knowing that Traps will continue protecting vulnerable applications. The Traps agent injects itself into individual processes as they start up. If a process attempts to execute any core attack technique, the corresponding exploit prevention module, or EPM, prevents that exploit, kills the process and reports details to Traps management service.
Figure 3: Multiple methods of exploit prevention
 By default, Traps policies are configured to protect more than 100 processes, each with dozens of proprietary EPMs. Beyond the defaults, you can protect all manner of processes and applications by simply adding them to the policy configuration. Processes that have run on the endpoint automatically show up in the management console, making it easy to protect them with the click of a button. This is especially useful for organizations running industry‐specific applications, such as point‐of‐sale systems, ATMs and SCADA systems.
By default, Traps policies are configured to protect more than 100 processes, each with dozens of proprietary EPMs. Beyond the defaults, you can protect all manner of processes and applications by simply adding them to the policy configuration. Processes that have run on the endpoint automatically show up in the management console, making it easy to protect them with the click of a button. This is especially useful for organizations running industry‐specific applications, such as point‐of‐sale systems, ATMs and SCADA systems.
A prevention-based endpoint protection strategy intercepts and blocks attacks before malicious activity occurs on endpoints. This means preventing an exploit from running or preventing malware from being executed. Such a proactive approach proves an ounce of prevention is worth a pound of cure.
Watch the webinar “5 Endpoint Protection Best Practices” to learn the essential requirements for endpoint protection, and how Traps advanced endpoint protection is simple to deploy and manage, providing a prevention-first approach that protects endpoints from malware, exploits and ransomware.