
Are session floods ruining your day? Build a dam with DoS Protection and Zone Protection to block those floods and protect your network zones, the critical individual servers in those zones, and your firewalls.
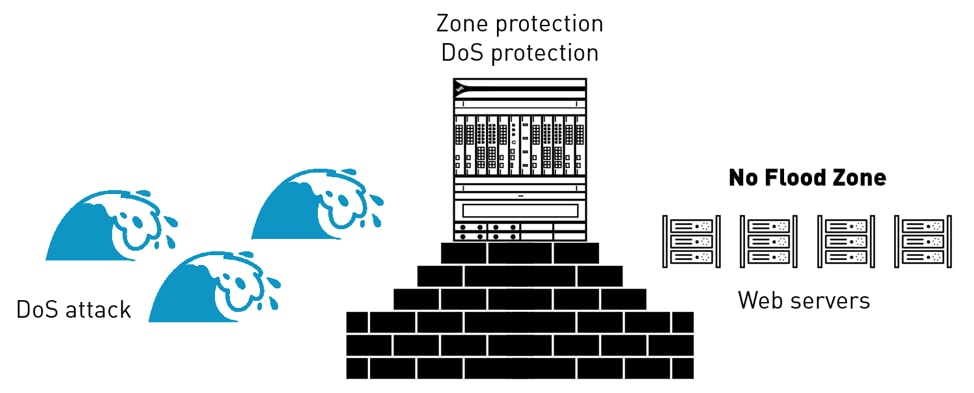
Adversaries try to initiate a torrent of sessions to flood your network resources with tidal waves of connections that consume server CPU cycles, memory, and bandwidth, disrupting services for legitimate users. Adversaries often target critical, internet-facing servers such as web servers to drown out internet connectivity and database servers to prevent you from connecting to your own information. Vaporize the flood by applying DoS Protection and Zone Protection so the firewall can protect zones and critical resources to ensure availability for legitimate users.
DoS Protection and Zone Protection Best Practices shows you how to plan for, deploy, and maintain DoS Protection and Zone Protection, including how to use a layered approach to flood prevention, where to position firewalls, where to apply DoS Protection and Zone Protection, and how to configure DoS Protection and Zone Protection profiles and DoS Protection policies. It also includes how to apply other zone defense capabilities such as Reconnaissance Protection, Packet-Based Attack Protection, and Non-IP Protocol Protection, as well as Packet Buffer Protection for the firewall. Don’t let adversaries turn your network into an ocean—use DoS Protection and Zone Protection best practices to construct a dam and keep your network out of the flood zone!
As always, you can find our content on our Technical Documentation site.