
You’ve taken the first step toward securing the valuable assets in your data center network by selecting physical and virtual next-generation firewalls from Palo Alto Networks.
Now how do you take the next step and implement best practices to take advantage of the next-generation firewall’s extensive features and capabilities to best protect your data center from malware, data exfiltration, and other cyberattacks? How do you maintain the trust and confidentiality of partner, customer, and employee data?
Learn about and implement a Data Center Best Practice Security Policy.

Get best practice advice about constructing policy rules that allow only the application traffic you explicitly want to allow in your data center, decrypting traffic, authenticating user access to data center applications and resources, and much more!
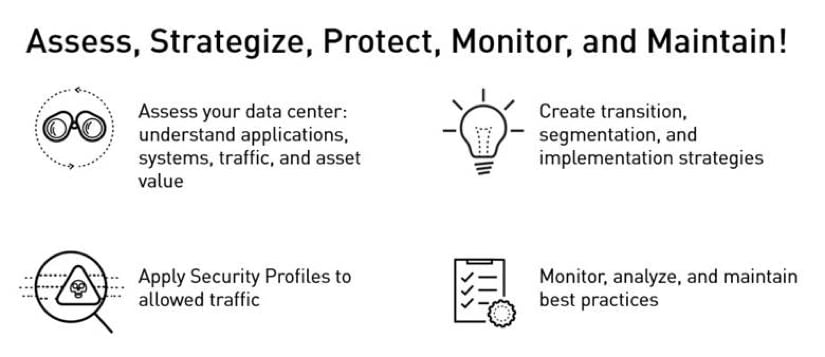
Data Center Best Practice Security Policy covers traffic flowing from users to the data center, from the internet to the data center, from the data center to the internet, and between applications and servers inside the data center (east-west traffic). Take a look and find out how to design and implement a data center best practice security policy!
Want more?
As always, you can find our content on our Technical Documentation site.
Happy reading!
Your friendly Technical Documentation team
Have questions? Contact us at documentation@paloaltonetworks.com.