Public cloud security is a shared responsibility but exactly who is accountable for what when it comes to the public cloud? Let’s begin with the facts:
- Public cloud refers to a set of virtualized resources (compute, networking, applications) operating on someone else’s computer, but that you control.
- Public cloud provides tremendous benefits, including agility, scalability, and faster access to innovative technologies.
- Security challenges in the public cloud mirror those faced within an on-premises data center (e.g. how to protect your applications and data from successful cyberattacks).
- Attackers are location agnostic. Their intent is to gain access to your network, navigate to a target, be it data, intellectual property, excess compute resources, then execute their end goal – regardless of whether it is on the network or in the cloud.
I think we can all agree on these points. But let’s take a closer look at security and determine who is accountable when it comes to the public cloud.
Public cloud vendors such as Amazon Web Services (AWS) and Microsoft Azure, profess that “public cloud data center infrastructures are more secure,” but what they are talking about is their data center infrastructure, on which you are deploying your applications and data. YOU are responsible for protecting the applications, access to those applications, and the associated data.
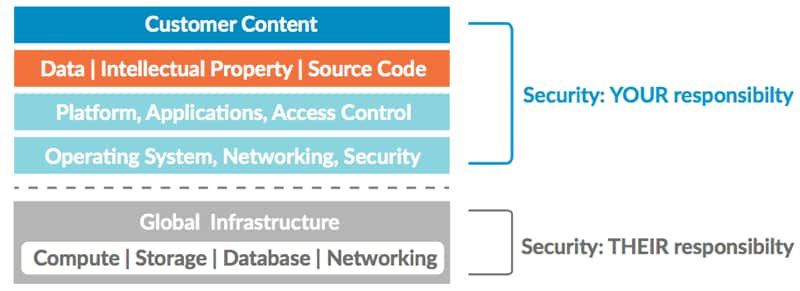
Breakdown of shared security responsibility in the public cloud
Let that sink in. YOU are in complete control of what security to implement and you must take steps to safeguard your content.
How Can You Secure Your Workloads in the Public Cloud?
Following are some of the key security capabilities required to ensure your applications and data in the public cloud are protected:
- Visibility and control over all traffic and applications in the public cloud, irrespective of port. Comprehensive traffic insight and control enables more informed policy decisions and better security.
- Safely enable applications, users and content. Allow the traffic and applications you want, deny all others, and grant access based on user need and credentials.
- Block lateral movement of cyberthreats (e.g., malware). Exerting application-level controls in between VMs reduces the threat footprint; policies can be applied to block known and unknown threats.
- Deploy new applications and next-generation security in an automated manner. Native management features (e.g. bootstrapping, dynamic address groups, fully documented XML API) enable automated policy updates and deployments.
- Policy consistency and cohesiveness across virtual and physical firewall form factors. A simplified, centrally managed network security management offering is a must.
The Palo Alto Networks VM-Series can help you accomplish all these things and more in the public cloud. But don’t take our word for it. Take a FREE Virtual Ultimate Test Drive and witness the virtual firewalls live and in action.
To learn more, get your guide to the Top 10 Public Cloud Security Recommendations.