Any organization that’s serious about preventing successful cyberattacks must be able to measure their prevention readiness, and this blog explains how we do that. The metrics ensure that leadership has confidence that the enterprise is operating as intended, with the modern capabilities required to prevent successful attacks.
The measurements we use are deliberate and intended to meet a rigorous standard, required to know yourself and know the enemy. Let’s review what General Sun Tzu said best in 500 B.C. His words are still true today in the cyber domain.
“Know the enemy and know yourself; in a hundred battles, you will never be defeated. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are sure to be defeated in every battle.”
Knowing You Are Properly Configured: Panorama Configuration Heat Maps
One thing we learned the more we performed our prevention posture assessment was a need to provide “factual” data to back up our prevention assessment assertions. For this reason, we created a family of Panorama configuration-parser heat maps intended to do exactly that.
The following heat maps provide different visual representations of actual prevention capability configurations on the Palo Alto Networks Next-Generation Security Platform. Together, they help us measure the extensible configuration for all areas of architecture we previously explained.
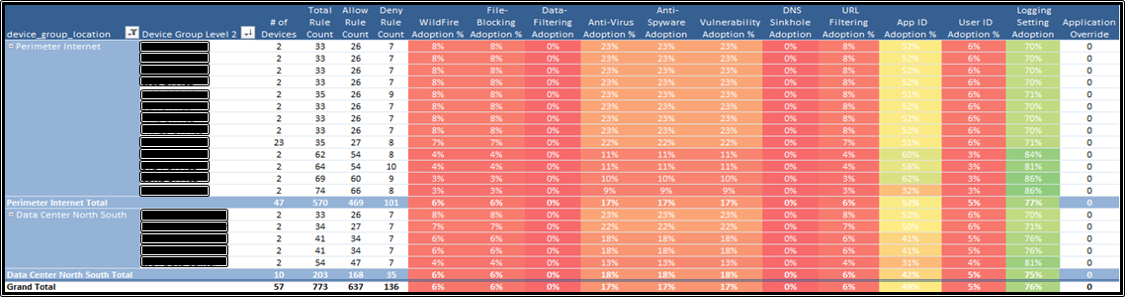
Figure 1 shows a view of capabilities and their configurations based on device group. Notice that we list the prevention platform capabilities across the top. The capability configuration adoption is provided below each capability. All of these configurations are based on “enable allow” rules configured on the platform, along with profiles that are activated on the rules. Don’t be discouraged by the color-coding. “Red” does not mean bad. Our goal with the heat maps is to determine if the IT and security teams configured the platform as intended. The color code can be of your choosing, and we ask customers to change it often to suit their needs.
This is a high-level heat map because it is limited to the device’s overall configuration without any detailed understanding of individual rules and capability profiles. However, it is still powerful because it helps IT and security professionals collaborate on how they are using the platform to protect and control their perimeter locations and data center locations.
Figure 1: Prevention capability adoption by device group example
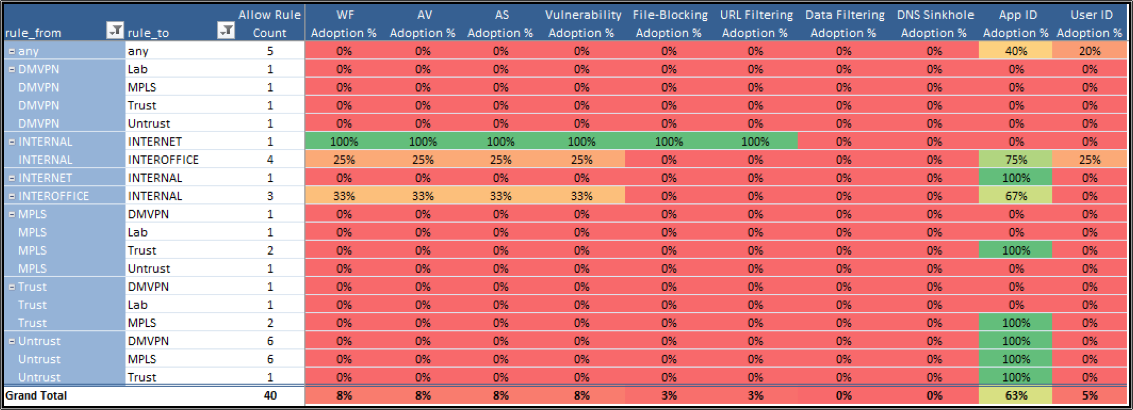
The second heat map, in Figure 2, gets much more granular in the platform configuration by showing specific zones. In fact, we noticed from practice, that most organizations have an intent of providing full protection and control for internet access points, but don’t really consider enabling protection on internal traffic. This trend is clear in the zone example.
From a prevention readiness perspective, we reiterate that it isn’t enough just to protect perimeter rules. Going through the capabilities using this view allows us to manage expectations with new customers and existing customers about making sure we confirm that the platform is configured and operating as intended in all zones. This builds confidence that customers get the most prevention capability possible from their investment, and it ensures we build continuous operational rigor around reporting prevention readiness.
Figure 2: Prevention capability adoption by zone example
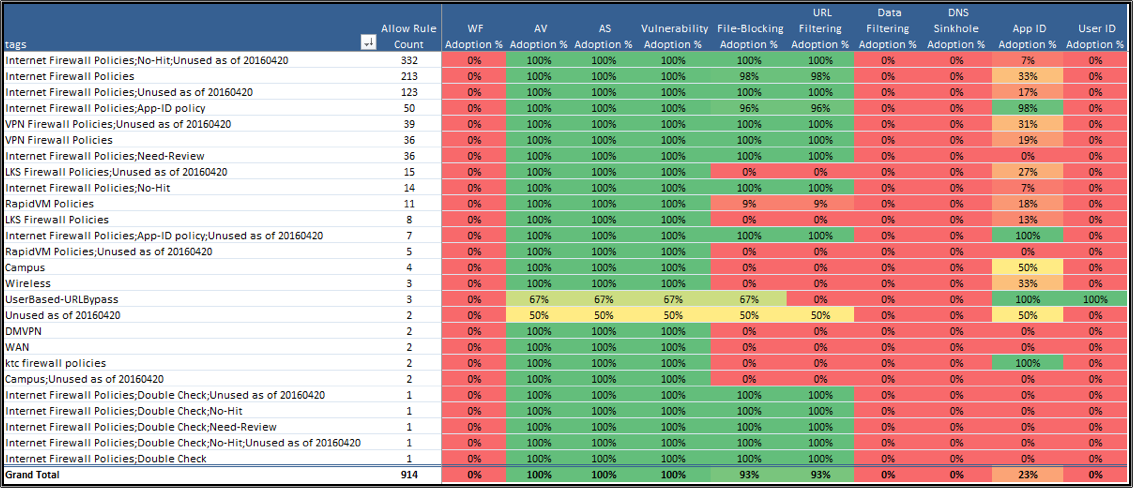
Our third heat map, in Figure 3, is based on tagging, and this is where things get really interesting. If you use tagging, you’ll like this view as a complement to the other heat maps. If you don’t use tagging, reach out to one of our representatives and work with them to build and implement a tagging strategy. It will be well worth your time to make sure you’re doing all you can to fully use the platform prevention capabilities.
Figure 3: Prevention capability adoption by tagging example
The configuration heat maps are intended to be simple so we can regularly communicate prevention readiness in a consistent manner. This way, we build confidence that we’re doing everything we can to take away an attacker’s ability to use known vectors, techniques, and tools.
Metrics to Build IT and Security Leadership Confidence
Our passion and dedication to prevention is paramount at Palo Alto Networks. As such, we know it is important to build IT and security leaders’ confidence that their enterprise is operating as intended and with a high degree of prevention readiness.
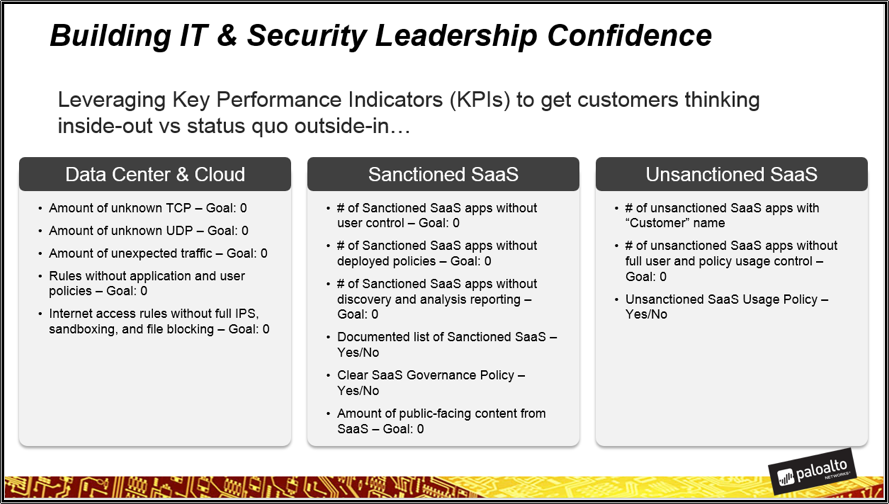
During our journey, we found some that metrics really hit home as leading indicators for knowing yourself and ensuring the enterprise is operating as intended. In Figure 4, we show these metrics because they are important to understand for a couple of reasons.
Figure 4: Building IT and security leadership confidence
First, all these indicators focus on the data center, cloud and SaaS area of architecture. This is intentional for the following reasons:
- We reinforce an attitude of inside-out thinking and prioritization.
- Every goal we achieve here is extensible to other areas of the architecture.
- All these items typically end up on the short list of customer priorities.
- It helps us keep things simple and prioritize efforts.
Second, all of the metrics in Figure 4 are easy for us to measure. Usually, we’ll focus on unknown UDP, unknown TCP, and unexpected applications operating on non-standard ports. In addition, we’ll compile a list of all SaaS applications and check them against your existing governance policy for SaaS. If you don’t have a governance policy, we’ll work with you to establish one.
Wrapping Things Up
Our representatives and partners are here to make prevention a reality across architecture. Prevention is in our DNA. Be sure to work with our advisors soon. They have tools to get you to the best prevention readiness possible, and we promise to continue to innovate and iterate on these tools in the future. These tools are all complimentary added-value items and part of our commitment to prevent successful attacks.
Have you asked for Panorama configuration heat maps yet? If you're an existing Panorama customer, why not? If you're a potential customer, request them soon. The only cost is some time for your team, but it will be time well spent, as professionals and leaders.