When I talk with customers about our GlobalProtect network security client for endpoints, there is often a moment in the discussion when we spend time discussing what VPN really means. Of course, everyone understands the literal meaning of VPN in terms of a textbook definition: virtual private network. The differences start to emerge due to the fact that many people think about what VPN technology does based on the functionality found in traditional VPN products designed to provide remote access. Those traditional VPN use cases were geared for an entirely different era, when applications were primarily hosted in the internal data center and users needed temporary remote access to those applications. The user would disconnect from the VPN when remote access was not needed, thus placing the user at significantly greater risk of attack. Organizations tolerated the increase in risk in order to get more performance due to the limitations in the VPN architecture.
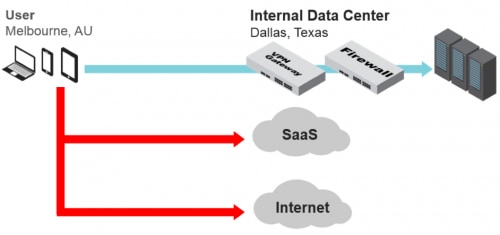
These conditions are no longer realistic, now that applications are shifting to the cloud and attacks targeting end users are becoming far more common. When mobile users are disconnected and accessing the Internet and SaaS applications, the organization loses visibility in network traffic, while makes the attacker’s work easier. Delivering an exploit to a vulnerable application, delivering malware from a filesharing application, tricking the user to visit a hostile domain, or conducting a phishing attack are just a few examples of things that are significantly easier for an attacker to do when there is no network security to protect the mobile workforce. Addressing the current state of affairs requires thinking about the difference between an architecture based on remote access and one focused on security. In a remote-access scenario, the goal is to bring the traffic back to an internally hosted application in the data center, no matter where the user is. Thus, the architecture stresses connectivity with security and performance being secondary criteria. The user is off the corporate network and needs remote access to the resources hosted in what may be some distant location, behind a corporate firewall. However, the traffic that’s not bound for the corporate data center (such as access to SaaS applications and the internet) would have to travel a considerable distance in the wrong direction if it passed through the tunnel. Many organizations forsake security in favor of performance by using a split tunnel that routes SaaS and internet traffic through the standard network interface. Thus, a dangerous set of conditions emerges in which the user has uninspected access to SaaS applications and exposure to internet threats.
Figure 1 Traditional Remote Access With a Split Tunnel
In contrast, the architecture for GlobalProtect differs from the traditional VPN because it is designed to extend the protection of the platform to users at all times. It uses VPN (as a technology for building a virtual private network), but our approach, compared with traditional remote access architectures, is markedly different.
Think about separating the concept of remote access and security. With remote access, the traffic is secure only if it passes through the tunnel, but distance to the internal data center creates performance issues, thus creating pressure to use the split tunnel.
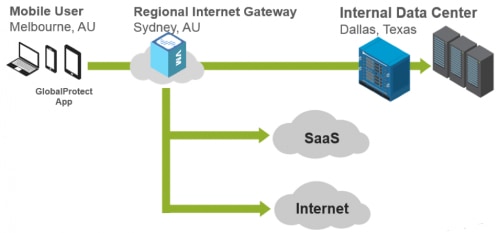
On the other hand, an architecture based on security must bring traffic to a point of inspection, namely a next-generation firewall. But the firewall does not necessarily need to be the one located at some distant data center, as is the case with remote access.
GlobalProtect supports this model by automatically connecting to the best available Palo Alto Networks next-generation firewalls that provide the best performance for the user. These firewalls are typically much closer to the user geographically, in the region where the user is located, thereby providing an internet gateway that delivers the protection of the platform for all traffic, whether to the internal data center, SaaS or the internet. These gateways are set up on next-generation firewalls and can be deployed in hardware or in the public or private cloud.
In addition, GlobalProtect supports the capability to auto-scale firewalls in AWS as seen in the lightboard video below.
This unique architecture automatically self-adjusts the number of firewalls that are available in a given region based on workload criteria.
With security in place and without performance degradation, GlobalProtect ensures that the organization maintains visibility and protection in network traffic for all users. It is also important to note that GlobalProtect still covers the remote-access use case as well, because the regional internet gateway can maintain a site-to-site tunnel back to the Internal data center. Organizations that deploy GlobalProtect can move beyond the limitations of the traditional VPN gateway and start securing themselves in a far more comprehensive manner.
If you’re thinking about how GlobalProtect fits with your organization, take a look at the following resources: