Following up on my initial post, AutoFocus: Your Answer to Actionable Threat Intelligence, this second post in the series provides another daily use case.
Searching From Firewalls
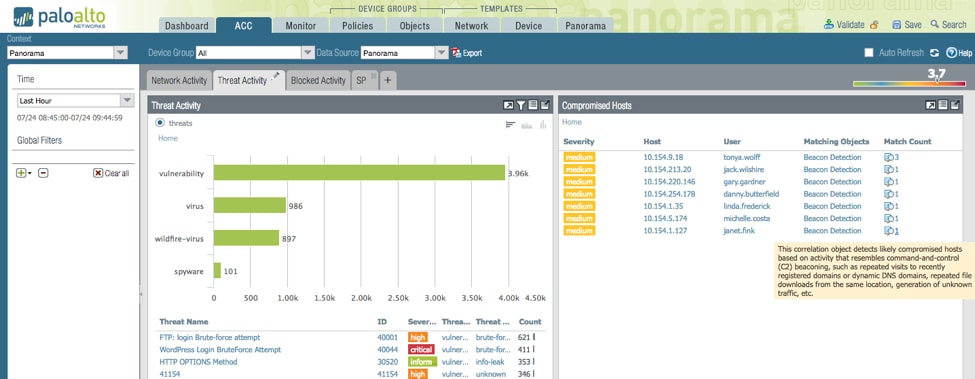
Something that happens from time to time is administrators will see remnants of malware coming from hosts inside the network but not the actual malware itself. This is a prime example of when administration teams should use actionable threat intelligence so they can arm themselves with information about what and whom they are up against, leading to shorter response times to an attack.
In this example we can see that there are beacon detections identified by the user “janet.fink.” In the ACC she is identified as having a compromised host. The beacon detection correlation object indicates that we are seeing known command-and-control traffic coming from this host; however, we did not see any of the associated malware. The probable cause is that the user had her device outside of the corporate network, was infected with something, and then brought it back into the network. This makes a good case for always-on VPN for corporate devices.
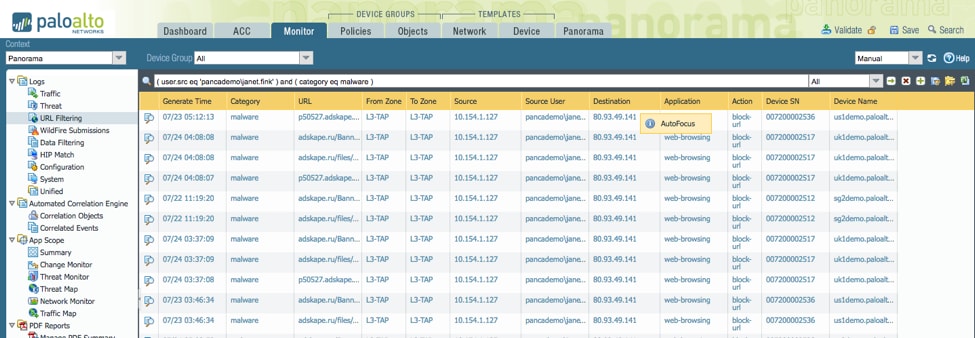
Drilling down into the correlation object and navigating to the source logs, we can see that Janet’s computer visited a known malicious domain over 100 times.
From here we can hover over any of these relevant attributes and query AutoFocus remotely.
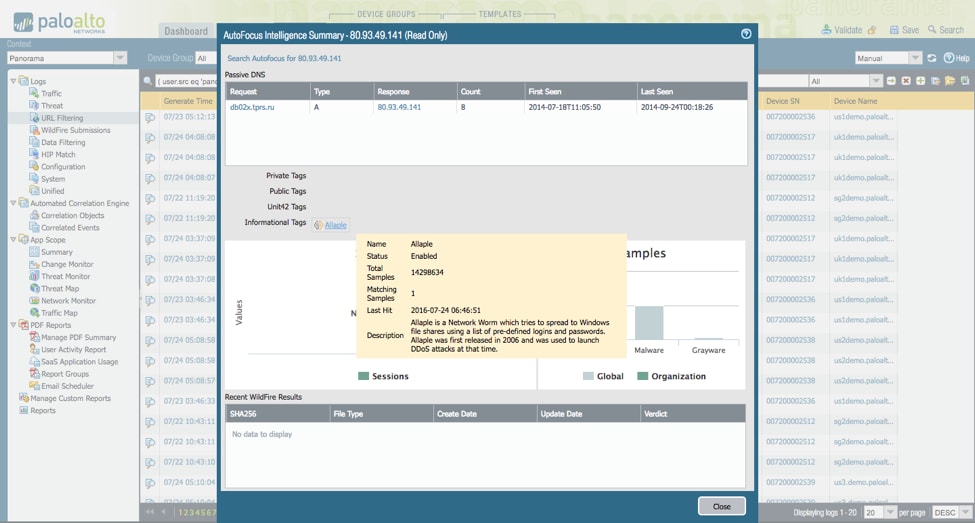
When AutoFocus is queried, a new results window opens. From here we can:
- Click the link to bring us directly to these results in AutoFocus to continue pivoting on the data.
- See that there is passive DNS information on this URL. The URL Janet visited does not actually match the previously identified URLs for this IP address, indicating that the attacker is maintaining the infrastructure and changing domains.
- See that the name of the malware family is Allaple. We are provided a description of the tag by Unit 42.
- See how many samples were identified in our network (0) and how many are globally viewable in AutoFocus (1).
This validates our initial suspicion that the user was likely infected outside of the network; otherwise, we would have data in WildFire to examine. Instead we are relying on the WildFire data from other organizations to determine from which malware this artifact comes.
Learn more about how AutoFocus threat intelligence service can help you accelerate analysis, threat hunting, and response workflows.