Not all data breaches are created equal. Some cost more, others less. Some are easy to detect, others difficult. As I was reading the Verizon 2016 Data Breach Investigations Report (DBIR), I was intrigued by the following statement:
“Insider incidents are the hardest (and take the longest) to detect. Of all the incidents, these insider misuse cases are the most likely to take months or years to discover.”
Months or years to discover. Let that sink in for a minute.
Who are these insiders? What is their motive? If these incidents take so long to detect, what’s the cost to the organization? What can security practitioners do to prevent these kinds of incidents?
I looked at some of the latest research materials and news articles on insider threats as I grappled with these questions. Here’s what I learned:
What is insider and privilege misuse?
An insider is not just the disgruntled Joe who didn’t get the raise he was expecting or the shocked Jane who was terminated last week.
An insider is anyone who has access to an organization’s valuable data. Under that definition, an insider could be an employee, partner, a third-party vendor, or someone whose access should have been revoked, like a recently terminated employee. The DBIR states that it could also be a combination of these actors:
“The Insider and Privilege Misuse pattern is one of the few that sees collusion between internal and external (or even partner) Actors. […] this year we had cases where instead of organized crime soliciting insiders to provide banking information, they went to the customer. It was actually external > external collusion to commit fraud.”
Insider and privilege misuse is common
Organizations use a variety of mechanisms to vet trusted insiders before allowing them access to valuable assets. The background check you went through before you were hired, the orientation training you attended, the access denied screen you saw on your browser, and the HR emails about acceptable use policies that you probably never read are all examples of such mechanisms. Even with these tools in use, insider and privilege misuse is common.
The DBIR states that insider and privilege misuse accounted for 10,489 total incidents, 172 with confirmed data disclosure. This equates to one confirmed data breach every other day. Further, if you are in the public, healthcare or finance industry, you are in the top three industries for the occurrence of such a data breach.
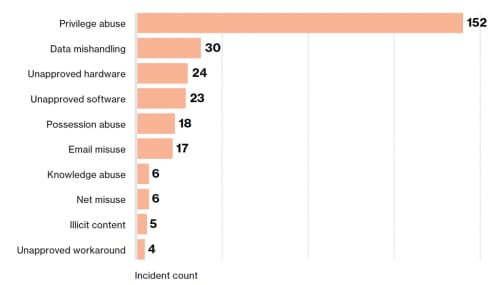
Within this category of data breaches, there are several types of incidents, as reported in the DBIR:
Because this type of data breach takes the longest to detect and resolve, it can also be costly.
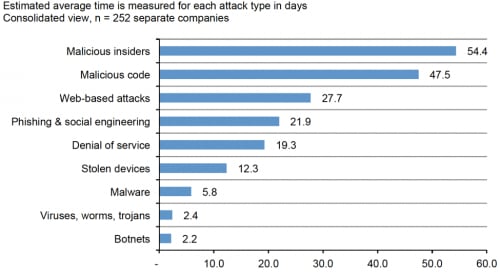
As I pointed out earlier, this type of breach takes the longest to detect. Months or years, if you recall. In addition, it can take the longest to resolve. Ponemon Institute’s 2015 Cost of Cyber Crime Study: Global measured how long it took to resolve different types of attacks after they were detected.
The study also measured the cost to the organization for each type of cybercrime.
“Time to resolve or contain cybercrimes increases the cost. […] Of all attack types, malicious insiders had the highest average annualized cybercrime cost weighted by attack frequency, at $144,542."
In paper Understanding Insider Threats based on a large study of 186 organizations, Gartner says that the biggest category of bad insider actors is:
"’Second streamers’ — so called because they seek to create a second stream of income or other benefits — misuse information for monetary or personal rewards.”
Prevention: It starts with you asking these 2 key questions
Wouldn’t you like to be the hero who saves your organization from such breaches that are so hard to detect and resolve? I would. But how? It really starts with you posing these two key questions to the security team as well as to the organization’s leaders – such that you might prevent these incidents and not have to detect them at all.
- What assets am I protecting?
- From whom am I protecting these assets?
As you answer the first question (i.e., the what), keep the following quote from Gartner’s Understanding Insider Threats paper in mind:
“Identify your organization's "crown jewels" — information and services that are critical to meeting strategic business objectives.”
Two points in the quote above are worth emphasizing:
- You may be protecting both information and services. Information could exist in the form of documents that may be physical or virtual, source code, people (yes, often people have key information that is not actually contained in documents), emails, and so on. Services are specific to your industry; for example, online trading, healthcare, research and hospitality services.
- Prioritize the information and services based on the criticality in meeting your strategic business objectives. Put simply, if an asset were to disappear tomorrow, will the core of your business continue to function? If yes, the asset doesn’t belong in the list of critical information and services.
As you move to the second question (i.e., the who), remember that an insider isn’t necessarily the pointy-haired boss (someone with special privileges), or the competent engineer. From the DBIR:
“When their roles were classified in the incident, almost one third were found to be end users who have access to sensitive data as a requirement to do their jobs. Only a small percentage (14%) are in leadership roles (executive or other management), or in roles with elevated access privilege jobs such as system administrators or developers (14%). The moral of this story is to worry less about job titles and more about the level of access that every employee has (and your ability to monitor them). At the end of the day, keep up a healthy level of suspicion toward all employees.”
I suggest you write down your own answers to the above questions — the what and the who — and then get the leaders in your organization to review your answers to make sure your understanding is accurate. With these reviews, a real danger is that the list of assets gets unwieldy. Remember the earlier point I made about criticality? Use it to keep the list manageable.
Call to action for all security practitioners
First, educate yourself and your users on the insider threat landscape. Here are some useful resources:
- Verizon 2016 Data Breach Investigations Report
- Ponemon Institute’s 2015 Cost of Cyber Crime Study: Global
- Gartner Understanding Insider Threats, May 2016 (must be a Gartner client to access)
In a follow-up blog post, I will cover the 5 steps for preventing insider and privilege misuse.
Call to action for the Palo Alto Networks security practitioners
Read this tech tips white paper to discover a step-by-step approach for enabling User-ID™ technology.