Traditional antivirus (AV) is not the solution to endpoint security – it is the problem. AV is no longer effective at stopping today’s cyberthreats and to prevent security breaches in your organization, you must protect yourself not only from known and unknown cyberthreats but also from the failures of any traditional AV solutions deployed in your environment. Today, we’re announcing enhancements to Traps advanced endpoint protection that empower you to replace your AV with real breach prevention.
In this post, I’ll go over some of the enhancements we’ve made to Traps. For a deeper dive, I encourage you to learn more about Traps, its new and updated capabilities, and how it replaces traditional antivirus with true prevention, by downloading the “Protect Yourself From Antivirus” white paper, or by joining our webinar to see Traps in action.
Traps replaces traditional antivirus with a proprietary combination of purpose-built malware and exploit prevention methods that protect users and endpoints from both known and unknown threats. With Traps, you prevent security breaches, in contrast to detecting and responding to incidents after critical assets have already been compromised.
The updated release of Traps eliminates the need for traditional AV by enabling you to:
- Prevent cyber breaches by pre-emptively blocking known and unknown malware, exploits and zero-day threats.
- Protect and enable your users to conduct their daily activities and use web-based technologies without concern for known or unknown cyberthreats.
- Automate breach prevention by virtue of the autonomous reprogramming of Traps using threat intelligence gained from Palo Alto Networks WildFire threat intelligence service.
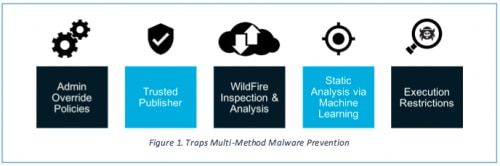
New and Improved Multi-Method Malware Prevention
Traps prevents malicious executables by maximizing coverage against malware while simultaneously reducing the attack surface and increasing the accuracy of malware detection. This approach combines several layers of protection that instantaneously prevent known and unknown malware from infecting your systems, whether they are online or offline, on-premise or off, connected to your organization’s network or not (Figure 1). Those layers include:
- Static Analysis via Machine Learning [new]: Obtain an instantaneous verdict on any unknown executable file before it is allowed to run, without reliance on signatures, scanning or behavioral analysis.
- WildFire Inspection and Analysis [improved]: Rapidly detect unknown malware and automatically reprogram Traps to prevent known malware by leveraging the power of Palo Alto Networks WildFire cloud-based malware analysis environment.
- Trusted Publisher Execution Restrictions [new]: Identify executable files that are among the “unknown good” because they are published and digitally signed by trusted publishers.
- Policy-Based Execution Restrictions [improved]: Define policies to restrict specific execution scenarios, thereby reducing the attack surface of any environment.
- Admin Override Policies [improved]: Define policies, based on the hash of an executable file, to control what is allowed to run in your environment and what is not.
Traps also quarantines malicious executables to prevent infected files from spreading to or infecting other users.
The combination of the above methods and capabilities not only prevents both known and unknown malware from compromising your systems but also enables you to fully customize the scope of prevention to meet your organization’s needs.
Improved Multi-Method Exploit Prevention
Traps uses an entirely new approach to prevent exploits. Instead of focusing on the millions of individual attacks, or their underlying software vulnerabilities, Traps focuses on the core exploitation techniques used by all exploit-based attacks. By identifying and pre-emptively blocking any exploitation technique the moment it is attempted, Traps prevents exploits from compromising your applications, including those developed in-house and those that no longer receive security support.
Traps implements a multi-method approach to exploit prevention, combining several layers of protection to block exploitation techniques (Figure 2):
- Memory Corruption/Manipulation Prevention [improved]: Identify and prevent the exploitation techniques that manipulate your application’s memory space before they can successfully subvert the application.
- Logic Flaw Prevention [improved]: Recognize and block the exploitation techniques that manipulate the operating system’s normal processes used to support and execute your applications.
- Malicious Code Execution Prevention [improved]: Identify and prevent the exploitation techniques that allow the attacker’s malicious code to execute, before they compromise your applications.
Traps protects applications and systems, whether or not they receive security patches, and regardless of network connectivity or physical location.
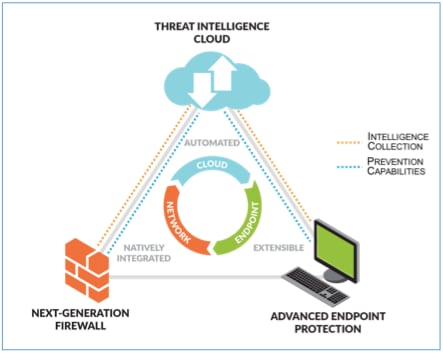
Automated Prevention via the Next-Generation Security Platform
Traps is the only endpoint protection offering that automatically converts the threat intelligence gained from a global community of over 10,000 WildFire subscribers and multiple threat intelligence sources into malware prevention.
When WildFire identifies an executable file as malicious, regardless of where that threat intelligence is gained, Traps automatically reprograms itself to prevent the execution of that file from that moment on. This process all but eliminates the opportunity for an attacker to use unknown and advanced malware to infect your systems because an attacker can use each piece of malware once, at most, anywhere in the world, and only has seconds to carry out an attack before WildFire renders it entirely ineffective.
As part of Palo Alto Networks Next-Generation Security Platform, Traps enables you and your organization to continuously apply the growing threat intelligence gained from thousands of enterprise customers, across both the network and endpoints, to your own environment.
Protect Yourself From Antivirus
- Download the “Protect Yourself From Antivirus” white paper
- Join us for the "Protect Yourself From Antivirus: Introducing the New Traps v3.4" webinar