Threat intelligence involves learning about new attacks, adversaries, campaigns, and malware families through distinct pieces of information often referred to as indicators of compromise, or IOCs. The more we make relevant information available to network defenders, the better the odds are that they will find answers to their questions. One key consideration for leveraging threat intelligence to improve an organization’s security posture is that it must be readily able to enforce new prevention-based controls.
Threat intelligence has traditionally been used by security operations centers’ incident response teams. As security awareness in organizations of all sizes begins to expand, most people realize that they want to know which alerts should be made a priority and which threats the organization is subject to. Who are the threat actors? There is a big difference between commodity and targeted attacks. Answering these questions can lead you to implementing new controls that allow you to better secure the environment.
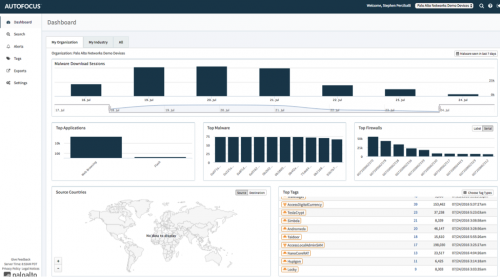
Enter AutoFocus. AutoFocus is the Palo Alto Networks threat intelligence service, which provides a window into billions of samples and threat artifacts collected from and correlated within our Threat Intelligence Cloud, including results from global WildFire data. The information allows security teams to quickly identify targeted that’s and pivot to relevant IOCs quickly, accelerating their analysis and response workflows. AutoFocus complements the Palo Alto Networks Next-Generation Security Platform, enabling searches from your Palo Alto Networks appliances into AutoFocus, or from AutoFocus into your Palo Alto Networks appliances. There is also an API that interacts with the data and feeds third-party security solutions. This level of usability means that a threat research team isn’t necessary to make use of the data. Anyone responsible for handling security incidents in the environment can make use of the data in AutoFocus.
In this post, we will explore a use case that will enable security operators to quickly identify what happened during an incident and to take action.
Searching From AutoFocus
Unit 42 is the Palo Alto Networks threat intelligence team that provides AutoFocus users access to world-class human intelligence, even if they don’t have a research team of their own. Unit 42 contributes to the AutoFocus community by researching malware families, campaigns, adversaries, exploits and malicious behaviors, and by compiling indicators of compromise into durable tags to identify malicious events.
To get started, it may be interesting to navigate through some of the research already done by Unit 42. Let’s assume Locky is something we have not investigated yet. By selecting this tag, we can get information about the research done by Unit 42 on this malware family.
Drilling into Locky provides us with all the search attributes associated with this tag. We can see that Locky is a ransomware payload, which is used to encrypt sensitive files or systems, then hold them until the victim pays the attacker. We also see that Locky is typically dropped by Dridex actors, which gives us a better idea of who is likely to be behind the attack. Ransomware is typically more of a commodity type of crime, in which the attacker’s goal is to get as many systems encrypted as possible, driving profits from their malicious activity.
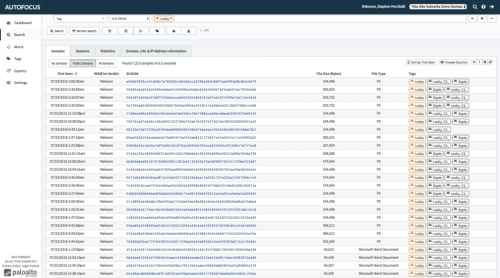
Selecting “Add Tag” to “Search” will bring up the results of a query that includes samples, sessions, statistics, and much more information about the malware. You can search through samples of data that came from devices owned by your organization via WildFire. You can also see samples made public by other organizations, dramatically broadening the lens.
This allows you to gain visibility into threats not directly observed by your organization, taking advantage of the community of WildFire and AutoFocus users. In this case, we will pivot into “Public” samples to further analyze the Locky ransomware.
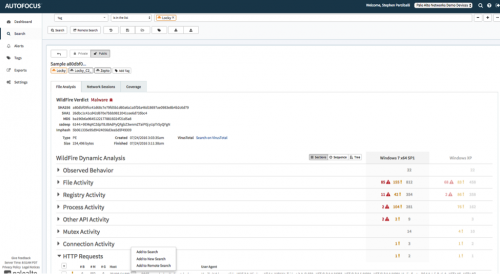
Finding over 7,000 variants seems daunting. It also demonstrates that file-hash-only identification is no longer practical. By drilling into the samples, we can see that there are patterns in the malware. These are the same similarities that Unit 42 used to create the tag. The infrastructure for the malware and most of what it does to the system once installed are the same each time it is deployed – primarily, that the file is obfuscated by changing a few bits to avoid hash-based detection.
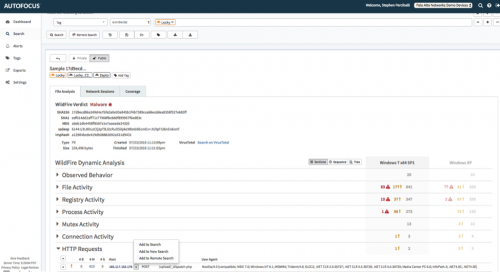
By drilling into one of the hashes, we can see everything that WildFire observed when detonating this malicious software on Windows® XP and Windows 7. From there we can drill into individual indicators of compromise and search our own appliances for evidence, as well as create new protections for specific high-value IOCs, such as IP address, DNS or URLs.
The remote search function allows you to add search filters specifically designed for Palo Alto Networks security appliances. You will first be prompted to choose which of your appliances to search. Finally the console for the specified appliances will launch with the search filters already in place.
In this case, we have selected our Panorama instance. Since the logs from all security appliances are being forwarded, we will have visibility into the entire network with one search.
When we search through all the various types of logs in Panorama, we are looking for a specific command and control server as the destination. The good news is that we did not find the command and control server for Locky in the network, meaning we have confirmed there is no active infection within the organization.