There are no flawless software systems or applications. Flaws often create security vulnerabilities that attackers can exploit to compromise systems and software. That is the primary reason software vendors issue vulnerability patches. So why do IT departments choose to delay (or even omit) the application of those patches to production environments? More importantly, how can security professionals prevent security breaches on endpoints that operate with unpatched and unpatchable software?
When IT and Security Compete
Generally speaking, IT and security functions have different, often competing priorities. The IT function is accountable for maintaining the operational availability and flexibility of systems and software applications. So a security solution (such as patching) that causes service disruptions on a regular basis is a difficult proposition in the eyes of IT decision-makers.
The security function, on the other hand, is responsible for ensuring the security of systems and software applications. In the eyes of a security practitioner, a vulnerable system that gets compromised can expose the entire environment. So applying security patches or upgrading older, less-secure systems and software is worth the occasional interruption if it protects the entire environment.
Still, even with the recent rise in the frequency and complexity of cyberattacks, the need for operational readiness and availability of IT systems and applications often trump the security function’s requests to apply vulnerability patches.
Why?
The answer is often complex and difficult to gauge. One simple consideration is that the process of applying vulnerability patches and upgrading production systems and software comes with challenges for IT organizations. It is a process that directly impacts the organization’s people, business process, and technology, often with unforeseen costs and downtime that are immediate and highly visible.
In contrast, the security benefits of applying vulnerability patches and upgrading production systems are rarely noticeable and typically less tangible.
Unless the organization is very risk-conscious and has a well-structured risk management function, avoiding the immediate pain of patching and upgrading often trumps the potential long-term security benefits.
Unpatchable Software Means Exposure – Forever
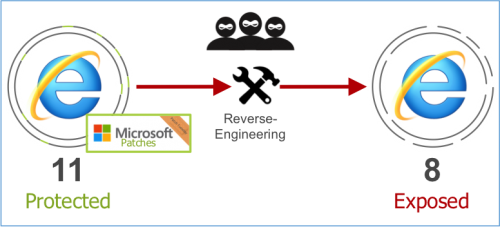
Applying vulnerability patches becomes a moot issue when the software in question has reached its end-of-support and will no longer receive patches from its vendor. This is now the case with Windows XP, Windows 8, Internet Explorer versions 10 and older, and Windows Server 2003.
In these cases, the risks associated with the unpatchable software increase exponentially over time. Not only will attackers continue to look for and identify new flaws that they can exploit in these unpatchable systems but they can also reverse-engineer vulnerability patches that vendors issue for newer versions of those software systems in order to identify unpatched vulnerabilities in the older, unsupported versions.
Without vulnerability patches from vendors, unpatchable software represents an unprotected attack surface that persists as long as the software remains deployed in the environment.
So what can security professionals do to secure endpoints that operate unpatchable software?
Eliminate the Need for Patching
Clearly as long as preventing security breaches on endpoints is dependent on patching and upgrades – activities that fall within the realm of IT authority – security professionals will be at a distinct disadvantage: they will be held accountable for solving a security problem without the authority to implement a key component of the solution.
This disadvantage is compounded in the case of unpatchable software that has reached its end-of-support because the necessary components (patches) are no longer available.
What if security professionals could eliminate the need for patching, regardless of whether those patches are available or not, while simultaneously solving the problem of preventing security breaches on the endpoint?
Traps Secures Unpatchable Endpoints
As discussed earlier, software flaws are the primary reason vendors issue vulnerability patches. Unpatched vulnerabilities present attackers with weaknesses that they can exploit. To prevent security breaches on endpoints that operate unpatched (or unpatchable) software, security professionals need to block the exploitation of those vulnerabilities.
That is precisely what Traps helps security professionals to accomplish.
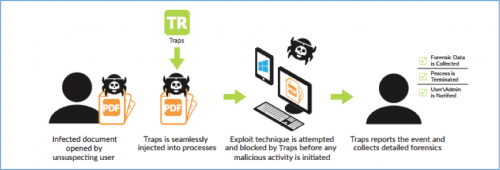
Attacks that exploit unpatched vulnerabilities typically place malicious code in a seemingly innocuous data file. When the user opens the file (e.g., a weaponized PDF file), the malicious code within that file leverages the vulnerability in the unpatched application and executes its code. Once the application is compromised, in most cases, the attacker can gain full control over the endpoint.
What makes Traps unique is its ability to block the core techniques that all exploits use to compromise applications. Traps focuses on these techniques, not the individual application vulnerabilities or the thousands of different attacks that exploit them. This is an effective strategy because all attacks that leverage unpatched software vulnerabilities rely on a small set of core techniques that change infrequently.
Traps blocks these exploit techniques completely, which means that the application is no longer vulnerable, even if the available security patches are not applied.
This also means that Traps can block unknown and zero-day exploits just as effectively as known exploits. To Traps, there is no distinction between them because Traps blocks the exploit techniques, not the individual exploits.
How does this work?
When an application starts, the Traps agent injects itself into the application process. This injection is entirely seamless to the end user. When the weaponized data file that the attacker has developed to exploit a software vulnerability begins to execute an exploit technique, the Traps protection modules block the technique and cause the exploit attempt to fail.
When Traps prevents such an attempt, the Traps agent terminates the process, collects various forensic data, and reports the details of the attempt to the appropriate security managers.
Traps eliminates the need for patching, regardless of whether those patches are available or not, while simultaneously solving the problem of securing the endpoint.
This is only a fraction of the total capabilities and methods that Traps uses to prevent security breaches on the endpoints. The malware prevention capabilities, threat intelligence sharing, and application execution controls of Traps are just as innovative, comprehensive and effective.
To learn more about Traps and how it can help you to prevent security breaches on endpoints – especially those that operate unpatched and unpatchable software – watch our webinar on Internet Explorer End-of-Support or download the Traps Technology Overview white paper.