Today is Back to the Future day, and the date above, as all fans of the iconic movie know, is what was programmed into the DeLorean time machine. The concept of time travel has long fascinated me, and thinking about this special day got me also thinking about how we deal with cyber threats.The approach to endpoint security still relied upon by most organizations has been largely unchanged for decades. That’s right, signature based malware detection is very old technology. It relies on prior knowledge of a threat in order to detect and eradicate it. Even newer approaches require prior knowledge in the form of indicators of compromise (IOCs) or behavioral patterns to look for. This approach poses significant challenges when it comes to preventing security breaches. If your approach is based on detecting the fact that something bad has occurred, then how can you prevent that bad thing from happening? Do you need a time machine for that?
It turns out our researchers here at Palo Alto Networks have solved that problem. We launched Traps about 12 months ago with the goal to redefine endpoint security by providing the much-needed ability to prevent advanced threats on the endpoint. Traps has been performing amazingly well when it comes to preventing previously unknown threats, without the need for any product updates. The reason for this is because it focuses on preventing the core techniques that are used by all exploits. And we didn’t need a time machine to get there.
Let’s examine the evidence
Exhibit A:
A Traps customer in the banking industry recently reported to us that Traps successfully prevented an Adobe Flash exploit from April 2015. This, in and of itself, is not unusual because we know that Traps prevents exploitation of unpatched vulnerabilities all the time. The interesting part of this story is the version of Traps the customer was running. An early Traps customer, they still had a system running Traps v2.3.6, which was released about a year before this vulnerability and the associated exploits became known. So a version of Traps from March 2014, never updated, prevented a zero day exploit in April 2015.
Exhibit B:
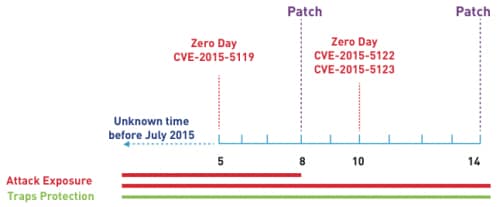
In July 2015 a series of Adobe Flash zero day vulnerabilities were disclosed as the result of an unfortunate data breach. The public was left waiting for patches while attackers began exploiting those vulnerabilities. Even organizations that deployed every security patch immediately upon release were left vulnerable for weeks. However, those organizations running Traps were never vulnerable, regardless of whether patches were deployed. Traps simply prevented the exploit techniques leveraged by all of these exploits.
Figure 1. Adobe Flash zero day timeline, July 2015
I’ll leave it to you to examine the evidence and make your own conclusions. Is the technology that underlies Traps fundamentally powerful and innovative? Or does someone on our R&D team have a DeLorean in the garage? Either way, Traps is redefining the endpoint protection market by enabling organizations to truly prevent unknown exploits and malware.
To learn more about Traps, visit our resources page.