Almost all UTMs or so-called next-generation firewalls have URL filtering capability, but they are not well integrated enough to utilize URL categories in a security policy. By taking advantage of URL categories, you will gain granular control of your network.
If you are unfamiliar with how to use URL categories in your security policy, the following tips can help. These tips provide you with powerful ways to protect your network and improve your bandwidth efficiency.
First, after logging into your Palo Alto Networks Next-Generation Firewall, click the “Policies” tab. Then, in the list of options on the left, click “Security.”
A “URL Category” column will appear (Figure 1).
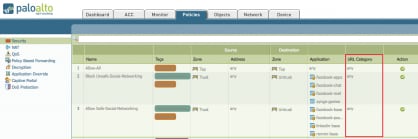
Figure 1: URL Category in the security policy.
If you do not see the URL Category column on your interface, it is most likely hidden from view. You can unhide it first by clicking the down arrow in any items such as “Action” or ”Profile”; I used “Action” this time (Figure 2). Then move your mouse on “Columns” and check the “URL Category” box near the bottom of the list.
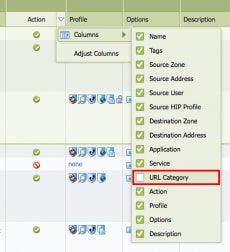
Figure 2: Unhiding the URL Category column.
The following examples show what can be done with URL categories.
1. Block file transfer from unknown sites.
![]()
Figure 3: Block download security policy.
An “unknown” URL most likely refers to a newly registered or unregistered URL, which is often used by cybercriminals. The files from “unknown” URLs can be considered high-risk files. You can block all file types from such “unknown” URL by creating the “block download from unknown” security policy shown in Figure 3. This means any files that might be transferred from an unknown URL will be blocked.
2. Decrypt SSL for specified URL category.
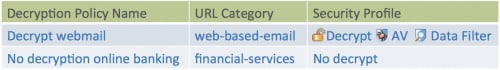
Figure 4. Decryption policies based on URL category.
In our 2014 Application Usage and Threat Report, we discovered 34% of all applications seen on enterprise networks use SSL. The risk of malicious activities and compromises are often hidden in SSL. Palo Alto Networks provides the ability to decrypt SSL based on URL categories. For example, you may want to decrypt and inspect webmail to block malware or sensitive files, but may not want to decrypt sensitive web activities such as online-banking to protect end-user’s privacy.
By applying decryption to the “web-based-email” URL category, you can decrypt webmail and apply other security features such as antivirus and data filtering.
In addition, you can choose not to decrypt online banking, by choosing the “financial services” URL category as “No Decrypt.”
3. Limit streaming media bandwidth during only business hours.
![]()
Figure 5: Limit streaming in quality of service (QoS) policy.
Our 2014 Application Usage and Threat Report also found that photo and video sites consumed 15% of all bandwidth we studied -- 7.5 times greater than that consumed by email. To improve productivity and bandwidth efficiency, you can limit the bandwidth for streaming media by creating a quality of service (QoS) policy. You can set maximum throughput for this policy and a schedule can be defined so that the QoS policy is effective only during business hours.
To learn more about web security, please visit our resource page, “Control Web Activity with URL Filtering.”