Here’s a roundup of this week’s top Palo Alto Networks news.
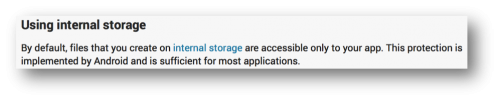
Insecure Internal Storage in Android: Palo Alto Networks researcher Claud Xiao demonstrates how an attacker can bypass Android protection to gain access to usernames, passwords and other data.
Palo Alto Networks examines the CHS breach and Heartbleed exploitation, another example that reiterates how serious this vulnerability is and how critical protection against it remains.
Last week we reported on attacks observed against East Asia that used Google Code for command and control (C2). As follow-on to that work, we pivoted on the C2 indicators of compromise within our WildFire platform, looking for additional malicious activity. Check out the sample that caught our attention.
Take a look back at the announcement of Unit 42, the release of its 419 Evolution report and the threat intelligence team’s appearance at Black Hat.

Find out what the expansion of our Global Distribution Agreement with Westcon Group means for Palo Alto Networks and our customers.

Next week we’ll gather in San Francisco for VMworld. Here’s a quick glimpse of where we’ll be, including our scheduled live demonstrations, presentations from Nir Zuk, and more. You can also experience our integration with VMware NSX up close and personal to find out how Palo Alto Networks Next-Generation Firewalls secure the software-defined data center.

We’re a finalist for five categories in this year’s Computing Security Awards, including Security Company of the Year and New Product of the Year! Vote Palo Alto Networks today.
Check out Rene Bonvanie's podcast with Crimson Marketing examining the five uses of marketing analytics to increase revenue.

Rick Howard spoke with Help Net Security during Black Hat USA 2014 to discuss the ever-changing role of the CSO at the executive level.

Here are upcoming events around the world that you should know about:
- When: August 24, 2014 from 4:00 PM - 7:00 PM PST
- Where: San Francisco, CA
2014 Cyber, Identity and Financial Threats Symposium
- When: August 26, 2014 from 8:30 AM - 5:30 PM GMT+10:00
- Where: Sanctuary Cove, QLD
Demo - näe mitä seuraavan sukupolven tietoturva tarkoittaa käytännössä [Finnish]
- When: August 26, 2014 from 3:00 PM - 4:00 PM EET
- Where: Online
Expose the Underground [Dutch]
- When: August 26, 2014 from 9:00 AM - 2:00 PM CET
- Where: Zwolle
Palo Alto Networks demo - näe mitä seuraavan sukupolven tietoturva tar [Finnish]
- When: August 26, 2014 from 3:00 PM - 4:00 PM EET
- Where: Online
The Fraud & Cyber Crime Group Symposium
- When: August 26, 2014 from 7:00 AM - 5:00 PM GMT+10:00
- Where: Gold Coast, QLD
- When: August 27, 2014 from 10:30 AM - 2:30 PM EST
- Where: Jessup, MD
- When: August 27, 2014 from 9:00 AM - 10:00 AM PST
- Where: Online
From Simple Scams to Silver Spaniel Attacks
- When: August 28, 2014 from 11:00 AM - 12:00 PM PST
- Where: Online
Opplev styrken i Next-Generation Brannmurer [Norwegian]
- When: September 3, 2014 from 1:00 PM - 2:00 PM CET
- Where: Online
- When: September 3, 2014 from 9:00 AM - 10:00 AM PST
- Where: Online
![EBA6A446-C190-439C-9DFB-A5B9FA842532[27]](https://www.paloaltonetworks.com/blog/wp-content/uploads/2014/08/EBA6A446-C190-439C-9DFB-A5B9FA84253227.png)