The latest Application Usage and Risk Report shows that when at work, Facebook users exhibit passive, voyeuristic usage patterns as opposed to a more active game playing or posting usage pattern. This activity pattern indicates that the “productivity loss associated with games or posting” is somewhat overblown. Inbound and outbound security risks DO exist, however, a non-productive employee is just that, non-productive; social networking is just one of the tools used to avoid work.
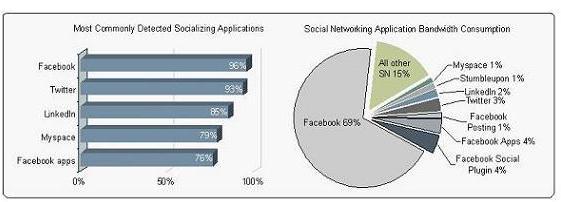
Categorically, an average of 5 different social networking applications (out of 51 total) were found in 95% of the 723 participating organizations. Facebook was the most commonly found at 96%. This near ubiquitous use of social networking contradicts the recent surveys touted in the press that show 50% or more of the organizations are blocking these applications. A 46% discrepancy far outside the margin of error and demonstrates the value of network analysis (reality) and survey data (perception).
Looking more closely at Facebook, shows the sheer dominance of Facebook. The four unique applications (Facebook, Facebook Posting, Facebook Apps and Facebook Social Plugins) consumed 78% of the total social networking bandwidth (3.9 TB). The remaining top four (Twitter, Stumbleupon, Linkedin and Myspace consumed a mere 7% with the remaining 43 social networking applications were left to share the remaining 15% (1.1 TB) of bandwidth. Pretty dominant don’t you think?
A more in-depth analysts of the Facebook specific traffic indicates that users are:
- Voyeuristic: While at work, users like to watch, which means that they are not playing games of posting furiously, which weakens the “lost productivity” argument against Facebook dramatically. The traffic patterns strongly suggest that Facebook users login to their wall, and keep it running all day, regardless of whether they are actually watching. This pattern is no different than opening an instant messaging application, or an email application and leaving it open all day. Make no mistake, there are other business and security risks associated with watching, but the potential productivity loss is small.
- Playing games less than originally thought: Comparatively speaking, Facebook Apps (games) represents a scant 4% of the traffic.
- Posting only occasionally: Facebook Posting represents an even smaller 1% of the traffic, yet the small amount of use should not minimize the risks in terms of what users are saying about work related subjects such as current projects, travel plans, and company status.
A Hidden Risk: Next-Gen Social Engineering?
Social networking application usage and adoption rates have accelerated to unprecedented levels with much of the growth driven by Facebook. The broadcast nature of the social networking distribution model represents significant outbound risks in terms of what a user says about the company, their projects, their travel plans, or company status on their social networking pages. An article earlier this week on SecureList highlights a real world example of how cyber criminals can gather information about you.
Far more detail on social engineering 2.0 is included in the 2010 Verizon Data Breach Report. The report discusses how attackers patiently collected information on their targets, taking any length of time to collect the desired data points using a combination of traditional social engineering techniques, updated for today’s web 2.0 world. Social networking sites can help uncover corporate roles or answers to security questions (names of pets, celebratory dates, favorite sports teams). Hijacked social networking user credentials can be used to convince a user to click on a URL with embedded malware, thinking it was from a friend. The malware in turn collects data such as user names and passwords that is used to help achieve the objectives. Additional examples provided by the Shadow Server Foundation in their report, Shadows in the Cloud: Investigating Espionage 2.0, describes how attackers were able to compromise nearly 1,300 computers in 103 countries by convincing users to click a URL, download a document, presentation, or PDF file that has been sent by (supposed) friends or acquaintances.
What to do?
As each week goes by, Facebook is being viewed as an integral business component as opposed to the previous view of nuisance and waste of time. A perfect example is the recent announcement by Delta Airlines that they would be enabling reservations via their Facebook page. Another example is the US Army and their use of Facebook as another element in their recruitment efforts. The challenge that many security professionals are faced with is the fact that the rapid growth has caught everyone by surprise and the traditional, security best-practices response to surprises is try and block or control them while policies are developed and implemented. The challenge of course is the plain fact that speed of adoption and caution do work well together.
Like any application that is brought into the enterprise by end-users, blindly allowing Facebook may result in propagation of threats, loss of data and damage to the corporate reputation. Blindly blocking is also an inappropriate response because it may play an important role in the business, and may force users to find alternative means of accessing Facebook (proxies, circumvention tools, remote access, etc.). Organizations should follow a systematic process to develop, enable and enforce appropriate Facebook usage policies while protecting network resources.
